Cybersecurity teams face an overwhelming number of vulnerabilities, making it difficult to determine which threats need immediate attention. Without a clear strategy, they risk wasting time on minor issues while leaving critical exposures unaddressed.
This article explores two essential Forward capabilities—Exposure Analysis and Path Analysis—that help security teams focus on the most pressing threats and strengthen network defense. Combined with Forward’s Network Device Vulnerability Management capabilities, Forward Enterprise provides a powerful platform for proactively defending against security threats and enabling rapid response when vulnerabilities arise.
Exposure Analysis: Prioritizing Security Fixes
One of the biggest challenges in cybersecurity is knowing which vulnerabilities to fix first.
Forward Networks integrates with Tenable Security Center or Rapid7 InsightVM to provide a Risk Score-based prioritization. With Exposure Analysis, organizations can:
-
Compare security scanner data with network data – Ensure all hosts are properly monitored.
-
Focus on high-risk devices first – Sort hosts by Risk Score, addressing the most critical threats immediately.
-
Run Blast Radius analysis – Determine the potential impact if a vulnerable device is compromised.
With this approach, security teams can avoid wasting time on low-risk issues and concentrate on the most pressing threats.
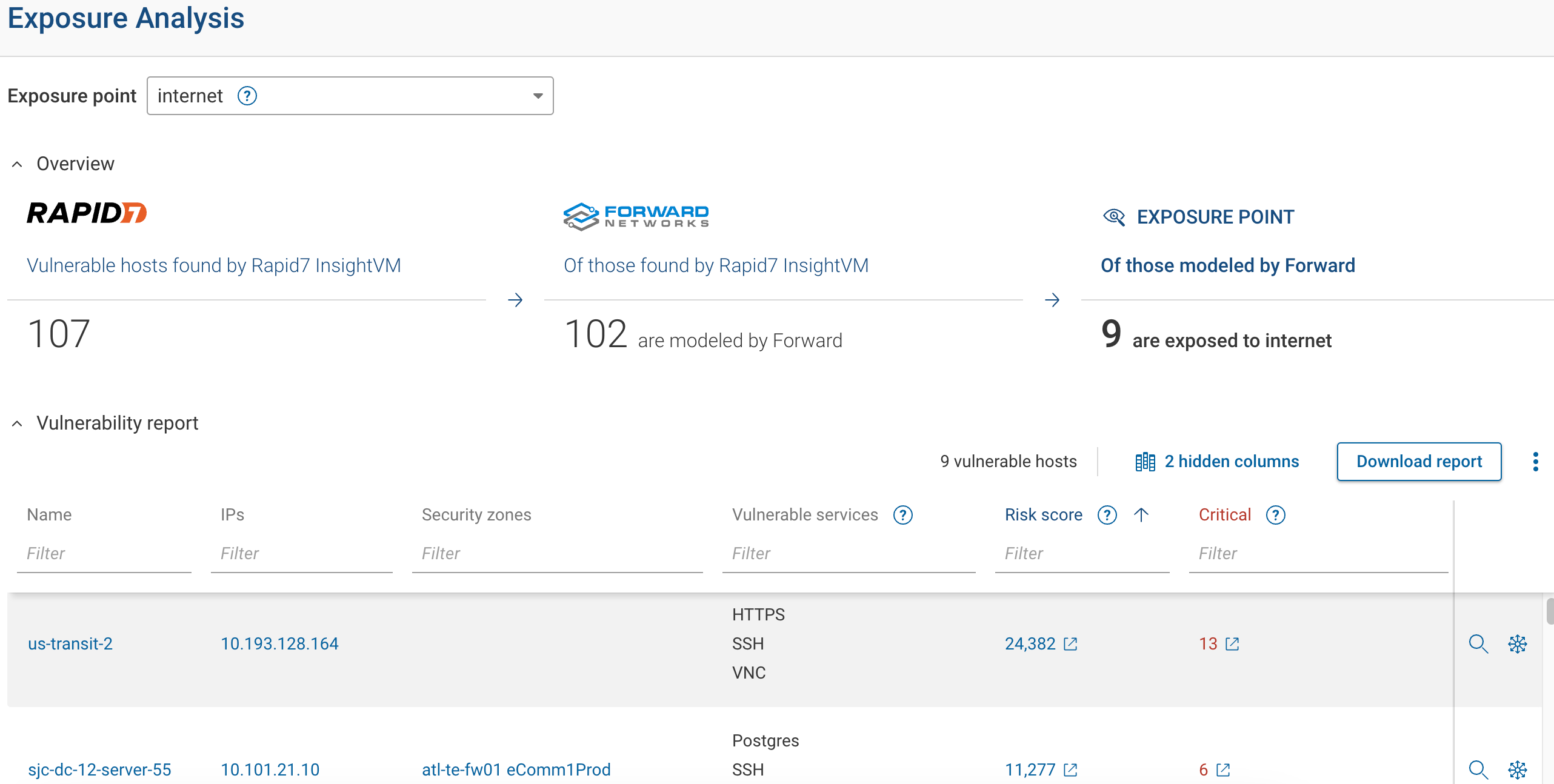
Leveraging the Exposure Analysis capability of Forward Enterprise provides organizations with the ability to prioritize exposure remediation by bringing visibility into what exposures need to be addressed immediately, and which ones can wait.
Path Analysis for Security Insights
The digital twin capability of Forward Networks collects configuration and state information from various network devices—routers, switches, firewalls, and more—to analyze every possible network path. This has two key benefits:
-
Validate proper network connectivity – Ensure paths exist between clients and application servers.
-
Assess risk exposure – Determine where a compromised device could move within the network.
If a SIEM detects a compromised host, security teams can:
-
See paths “from” here query – Instantly visualize where an infected host could spread.
-
Filter results – Narrow down analysis to the most relevant attack paths.
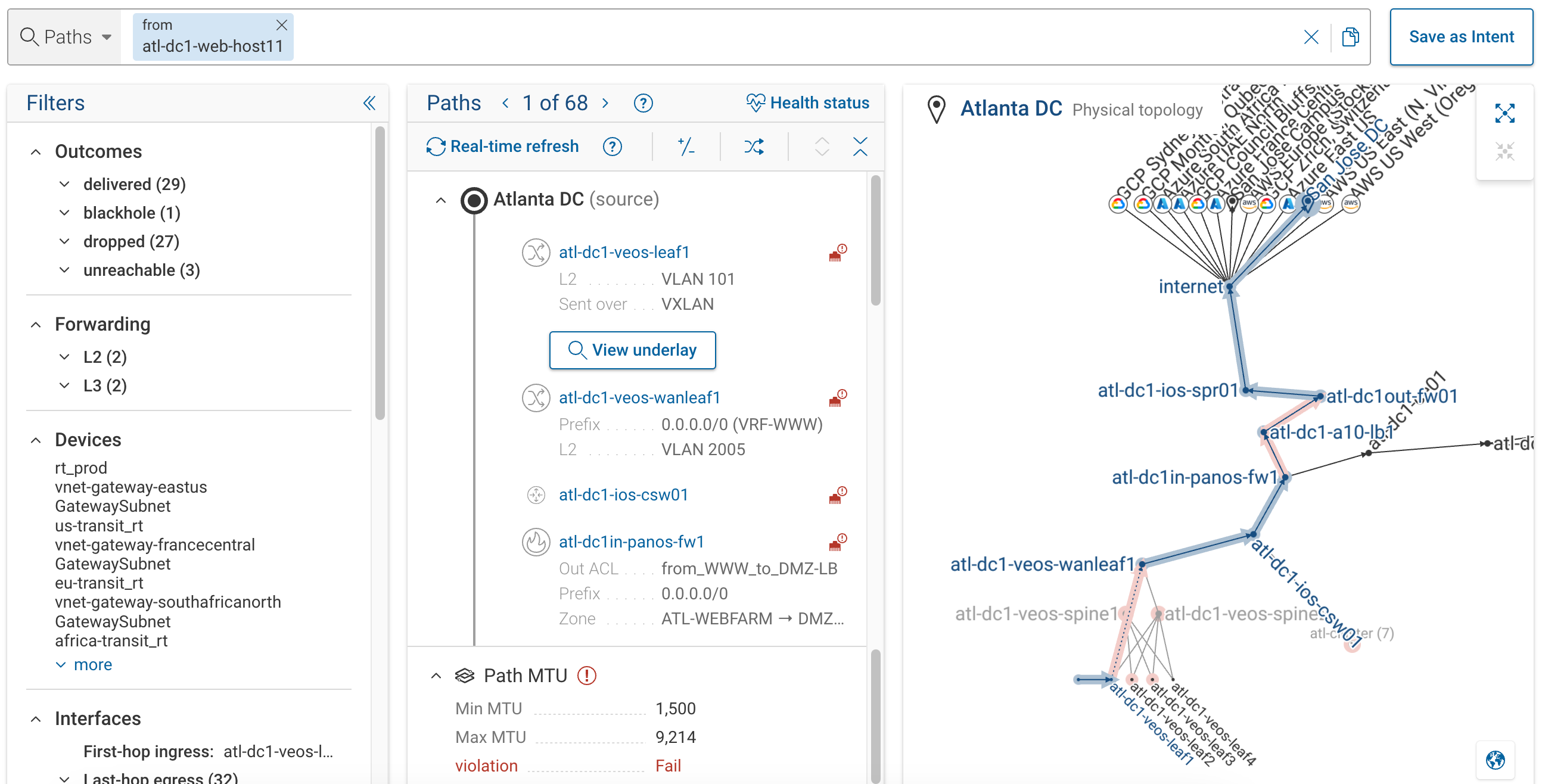
Prevent Lateral Movement with Blast Radius
A cyberattack doesn’t stop at just one compromised device. Attackers look for ways to move laterally across the network.
With Forward Enterprise’s Blast Radius feature, security teams can:
-
Simulate an attacker’s next steps – Enter a compromised host and see where it can connect.
-
Identify security gaps – Understand which devices are accessible based on firewall rules, IP protocols, and security zones.
-
Limit exposure proactively – Use the data to tighten security controls before an actual breach happens.
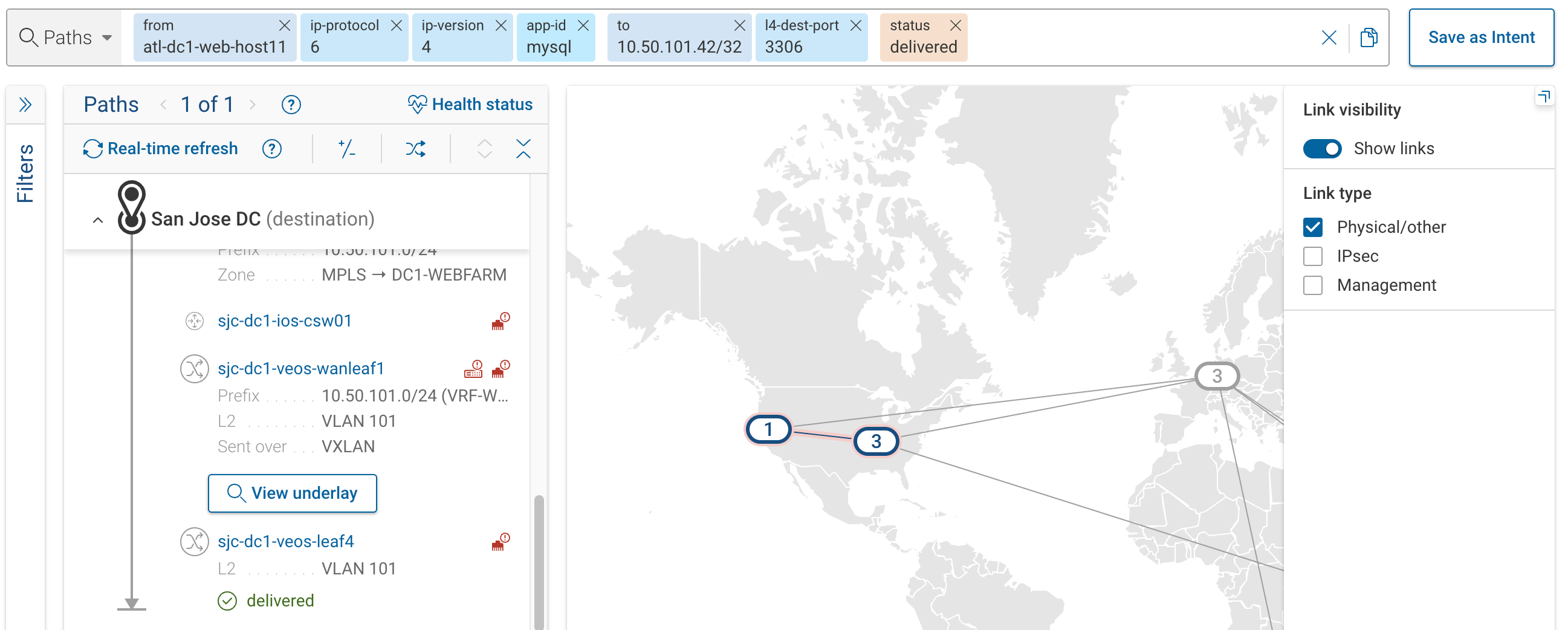
Blast Radius provides an attack path mapping that a malicious actor might use so you can rapidly respond to threats.
Stay Ahead of Threats
Threat Exposure Management isn’t just about reacting to attacks—it’s about preventing them before they happen. With Forward Enterprise, organizations can:
-
Gain full network visibility to identify all connected assets
-
Identify attack paths from at-risk devices to prevent lateral movement
-
Prioritize security fixes based on real risk assessments
By leveraging these capabilities, security teams can strengthen their defenses, reduce exposure, and stay ahead of cyber threats before attackers can exploit them.
Do you have additional questions about Forward Threat Exposure Management? Ask below!




