If you’re a network engineer familiar with the Forward Enterprise platform, you’ve probably used its core features like path verification, outage prevention, and troubleshooting. But have you explored its network device vulnerability management capabilities?
These Forward platform capabilities help organizations identify vulnerable devices before attackers exploit them. Together with Forward’s Threat Exposure Management, you have a powerful platform to protect against and rapidly respond to security threats. Let’s dive into key areas where Forward Enterprise strengthens network security.
Know What’s on Your Network: Inventory Management
A CISO from a major Forward Networks customer once said, “How can I secure my network if I don’t even know what’s on it?” That’s a crucial question. Many organizations lack full visibility into their network devices, which creates security risks.
With Forward Enterprise, companies can:
-
Discover all network devices – Customers often find more devices than expected when using the scheduled discovery feature.
-
Identify outdated hardware – Unmonitored devices may run end-of-sale or end-of-life software, increasing security risks.
-
Track vendor support status – Some devices may lack an active support contract, making them vulnerable to issues without proper assistance.
-
Verify assets for maintenance renewals – Cross-reference hardware serial numbers to avoid paying for decommissioned equipment.
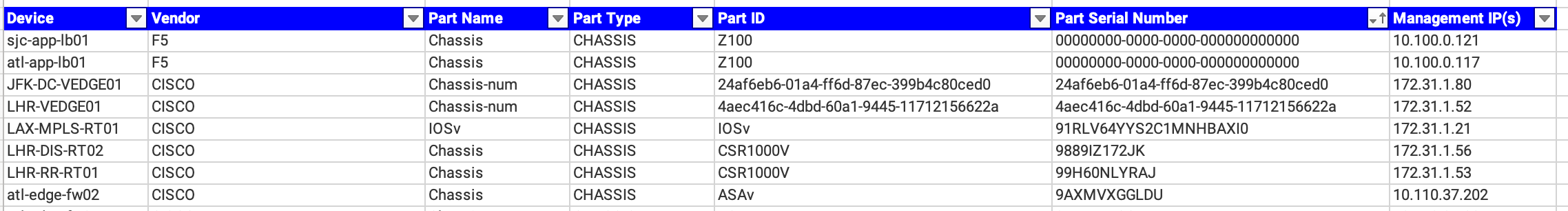
The screenshot below is an excerpt from a Forward Enterprise Device Hardware report that shows the serial numbers for different part types to include things such as chassis, routing engine, and line card. The information in this report can be cross-referenced to the serial numbers that are provided from a hardware vendor when it comes time to perform a maintenance renewal as it is not unheard of for a hardware vendor to request that a customer pay maintenance on a decommissioned asset.
Stay Ahead of Software End-of-Life Risks
Once you know what assets are on their network, you can leverage the end-of-life data analysis capability that the Forward Enterprise platform provides to make sure they are running versions of software that are supported by the manufacturer.
Forward Enterprise provides an end-of-life data analysis feature that supports multiple OS types, including:
-
Cisco IOS, IOS-XE, IOS-XR, NX-OS
-
Arista EOS
-
Juniper Junos OS
-
Palo Alto PAN-OS
-
F5 TMOS, Fortinet FortiOS, Check Point Gaia OS
This excerpt from an OS Support report provides dates for end of OS maintenance, end of OS vulnerability, and end of OS support.

This analysis helps companies:
-
See critical end-of-support dates – Know when OS updates will no longer receive patches.
-
Mitigate security risks early – Identify outdated software before vulnerabilities become a problem.
-
Plan upgrade cycles efficiently – Reduce unplanned downtime by proactively scheduling software updates.
Identify Vulnerabilities with the Network Query Engine (NQE)
Knowing what’s on your network is just the beginning—understanding vulnerabilities is the next step. Forward Enterprise’s NQE allows organizations to:
-
Detect open ports – Open RDP and SSH ports can be an easy target for attackers.
-
Analyze operating system vulnerabilities – Identify weaknesses before they are exploited.
-
Monitor cloud security risks – Run security queries for AWS resources that allow unauthorized access.
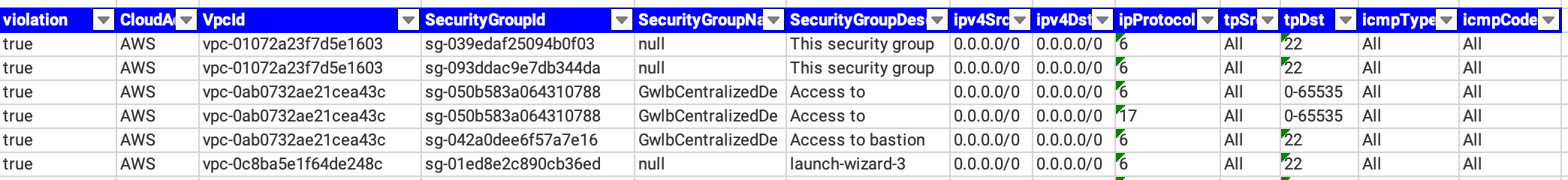
For customers that are leveraging the cloud collection capabilities of Forward Enterprise to collect against resources in AWS, the platform offers two NQE queries that look for cloud resources that permit either unfettered RDP and/or SSH access. The screenshot below shows a sample of one of these reports for SSH.
By leveraging these capabilities, security teams can take proactive measures before an attack happens.
Stay Ahead of Vulnerabilities
Threat Exposure Management isn’t just about responding to attacks—it’s about preventing them. With Forward Enterprise, organizations can:
-
Detect vulnerable devices and software
-
Prioritize security fixes effectively
By leveraging these capabilities, security teams can dramatically improve their organization’s security posture before attackers strike.
Do you have additional questions about Network Device Vulnerability Management? Ask below!




