Connecting the forward app to an Authentication source allows for granular connectivity to allow users to have the appropriate access to in the forward application. This applies to on-prem installations - not SaaS.
Prerequisites:
- A FreeIPA LDAP Source
- CA / Sub CA infrastructure (certificate Authority for the LDAPS source)
Requirements for LDAPS integration
To integrate LDAPS from FreeIPA (IPA) into the Forward Platform, the following data will be required or created:
- Root/Sub CA certificate chain
- A bind account for allowing Forward to run LDAP queries
- Groups defined for access controls (Network Operator, Network Admin, Read-only, Limited Read-only)
The Distinguished Name (DN) and Common Name (CN) will be required for the Bind Account and Groups
Create a bind account
Login to FreeIPA and navigate to the Identity → Users Tabs.
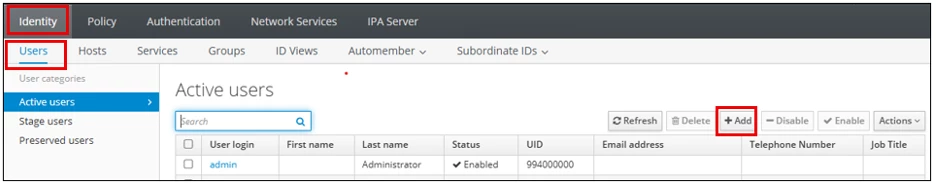
Here we will add a bind account - Click Add
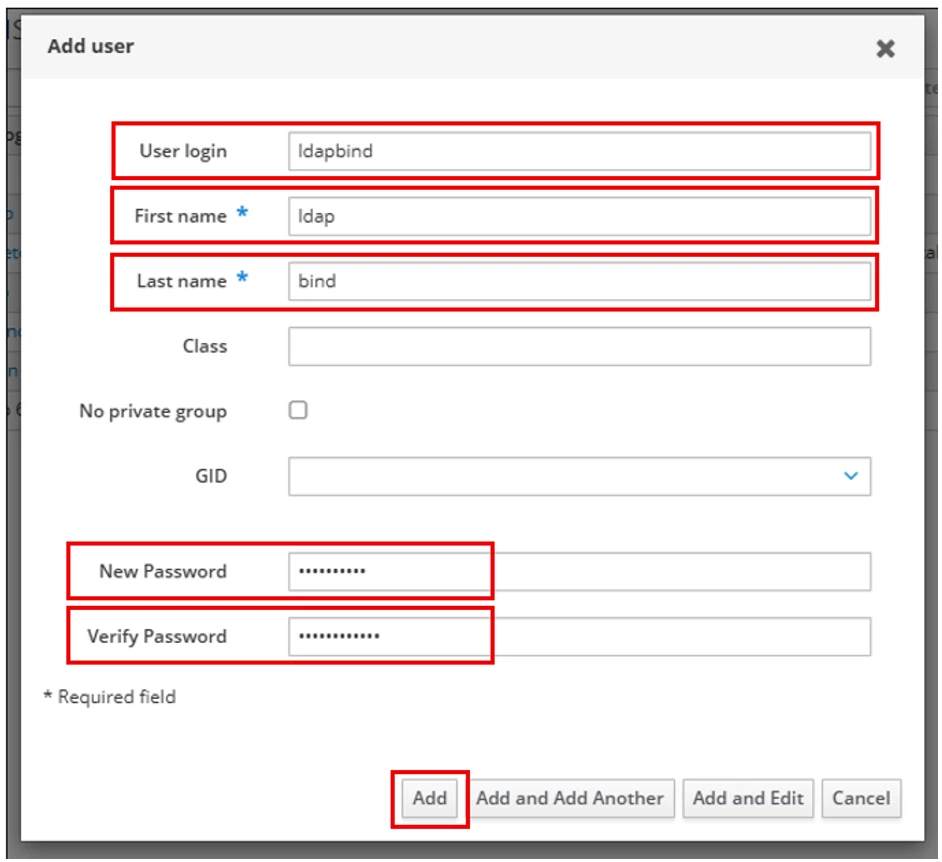
Fill out the highlighted fields and make sure that the initial password for this account is correct (not like in the picture).
After the account has been created, we can get all of the account details and attributes from the command prompt. From your IPA server (or any VM that is joined to the IPA server), type the following command:
kinit <username>
where username is the account used to create the account. You will be prompted for a password.
Then type the following:
ipa user-show <bind-account> --all
where <bind-account> is the account you just created. See the example below:
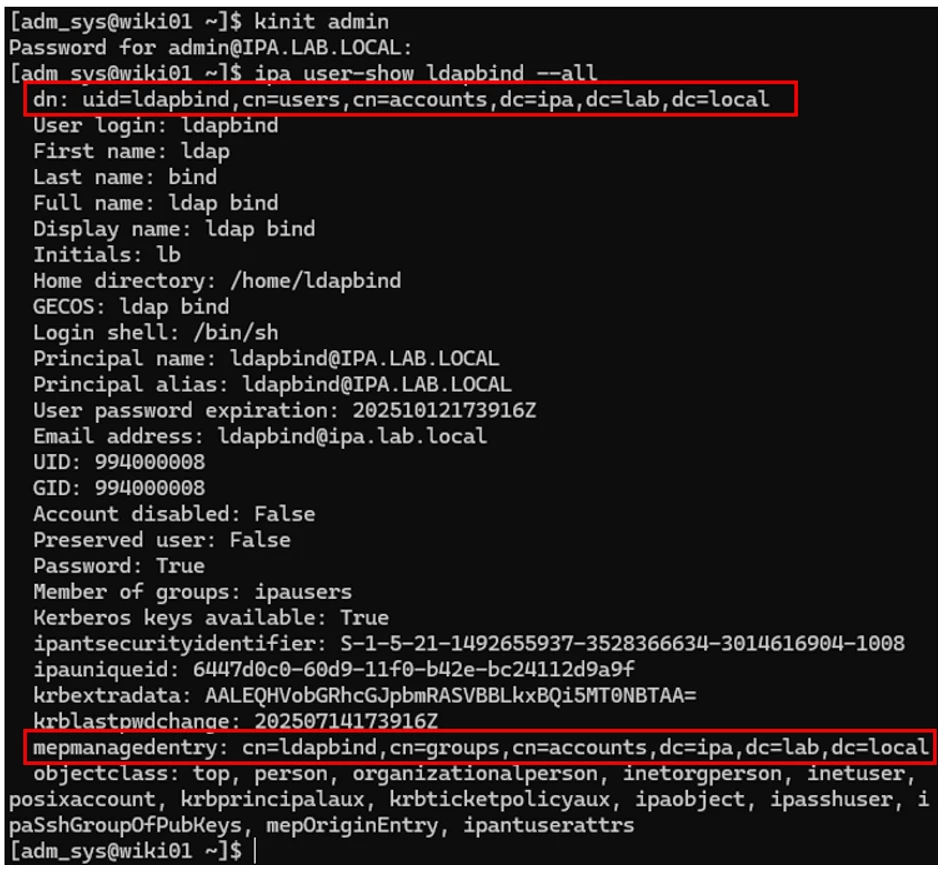
Note the DN field at the top and the mepmanagedentry at the bottom. We are going to use this information for the LDAPS groups connection.
***** NOTE ******
When a new account is created in IPA, the initial password is a “user must change password upon login” and will not work until you login to the web interface with the bind account and then set a permanent password upon login.
Collected your CA CHAIN
The next item we need is the certificate chain. The easiest place to find this is on your IPA server. The chain can be found :
/etc/ipa/ca.crt
You can cat this file and it should have at least two certs (Root and Subordinate). You may have more if you have multiple subordinates.
cat /etc/ipa/ca.crt
We will need to paste this into the forward platform:
LDAP Configuration
Login to the forward platform with an Admin account.
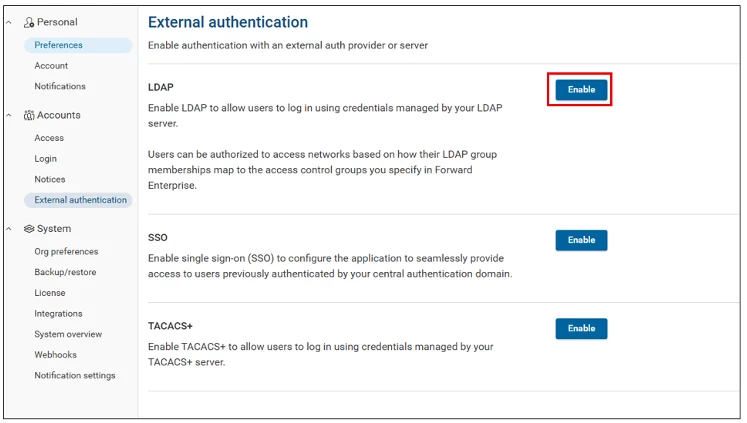
Navigate to Settings → Accounts → External authentication
Enable LDAP
Enter the following information for configuring the LDAP server:
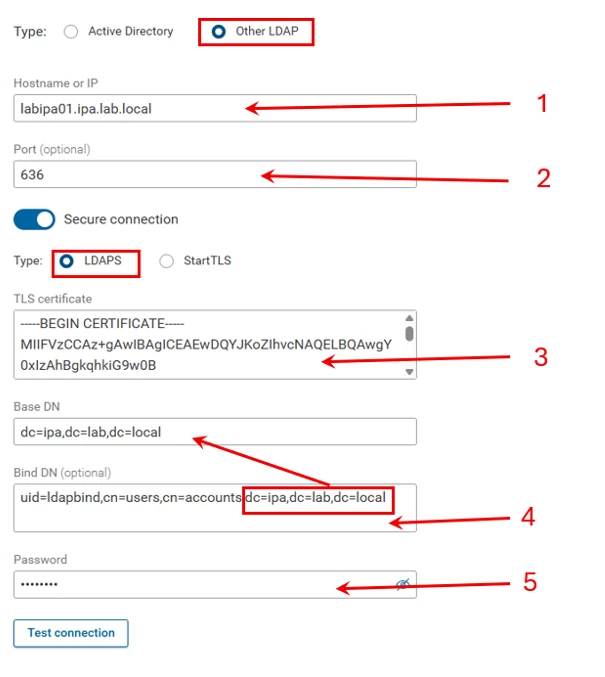
Select Other LDAP radial button
- Enter the FQDN of the IPA server for the LDAP connection
- LDAPS port is 636
Toggle the Secure Connection slider and select LDAPS - Paste the certificate chain from your IPA server into the TLS certificate box.
- Paste the bind account DN from the ipa user-show account from earlier into the Bind DN field.
At the end of the DN string will be entries that start with dc. Copy all of the dc entries and paste that string into the BASE DN field. - Enter the password for the bind account and click Test Connection.
SAVE CHANGES!
LDAP Users and Groups
The IPA user and group structure is flat unlike Active Directory so the entries in the next few field are static:
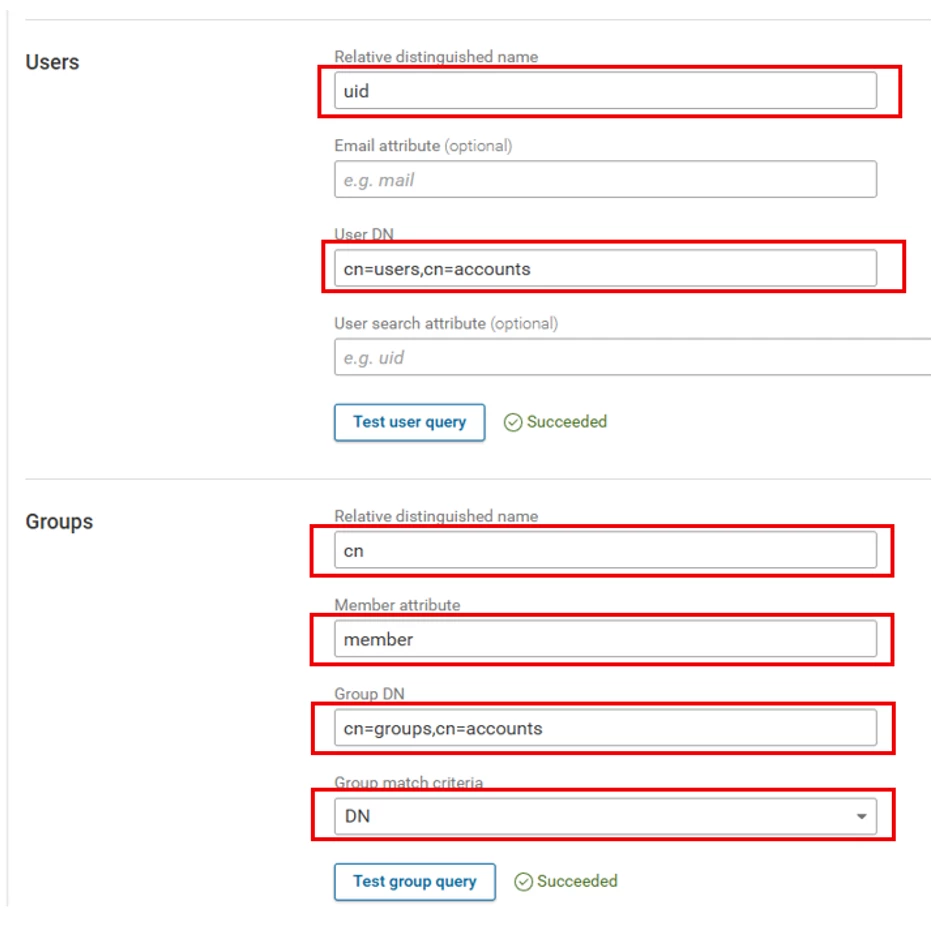
Please enter the above information in your LDAPS connection for FreeIPA. Note that the data for the groups section came from mepmanagedentry of ipa user-show command
Save Changes!! At the top of the page
Setting up Access Control Groups
In order to setup tiered access to the Forward platform, access control groups are tied to IPA groups to allow users to be assigned to different access levels.
There are four roles within the Forward Platform:
- Net Admin = Administrator level access
- Net Operator = Operations level access
- Read-only = User level access
- Limited Read-only = Limited User level access
Create these groups up within FreeIPA:
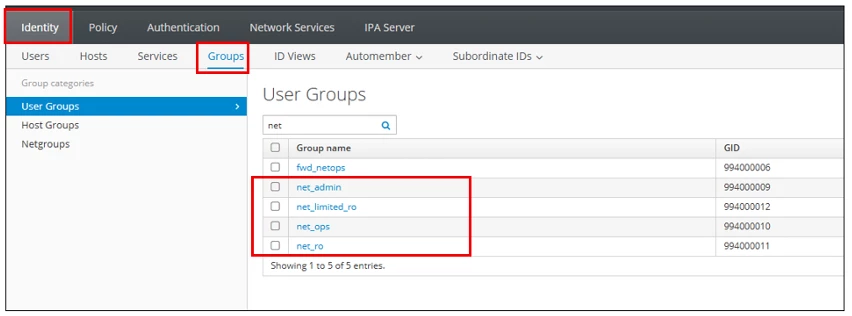
Creating a group is as simple as clicking the add button (not pictured to the right) and naming the group.
You must add users to one of these groups in order for user to login.
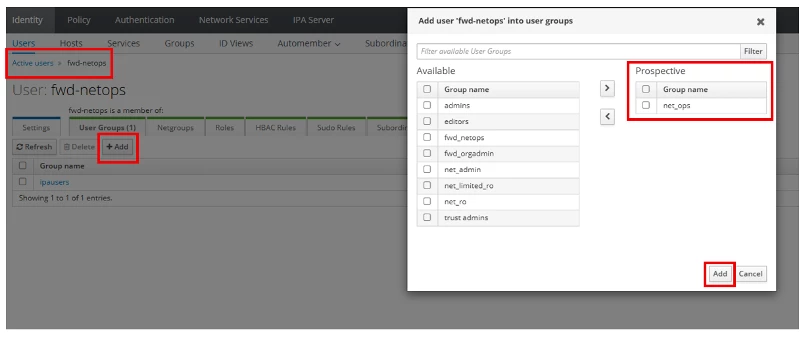
Add these groups to the forward platform and associate them with the appropriate Role
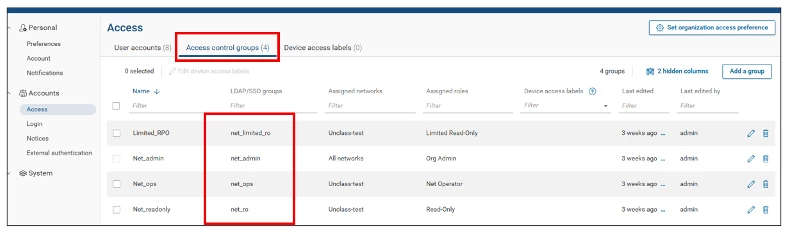
Here the groups from FreeIPA and mapped to groups within the forward platform.
Testing LDAP Authentication:
There is not a test user account login on the LDAP configuration page. To test a user account login, you must log out of the platform and login with the LDAP created account