On May 21st we have shown the integration between Forward and NetBox in a joint webinar.
UPDATE: The webinar recording is now available on YouTube:
https://youtu.be/TSX14uke1NE.
The description includes a link to the webinar slides and the GitHub repository.
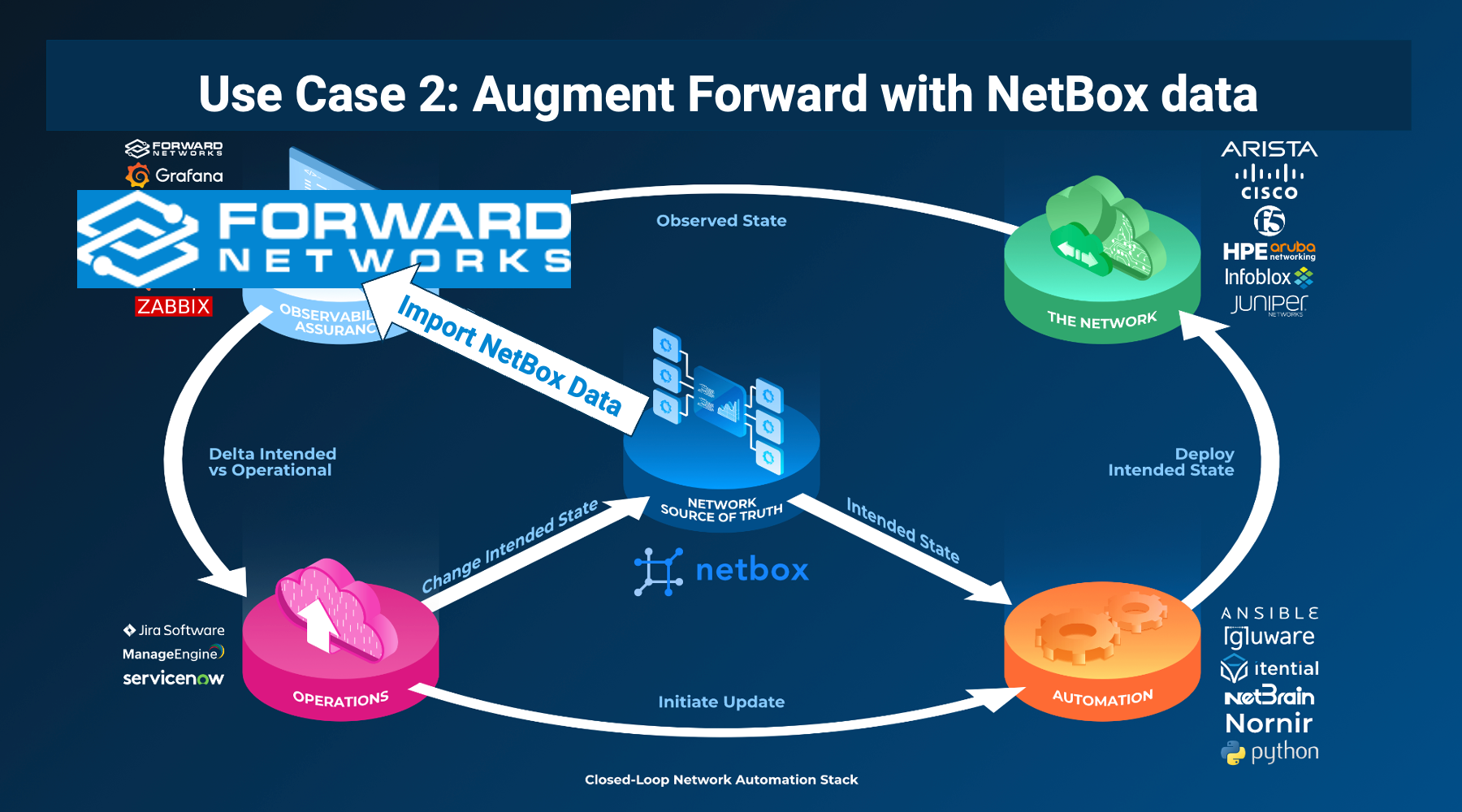
The integration is part of the NetBox’s Network Automation Architecture framework where Forward provides the Observability and Assurance piece, as shown in the picture below:
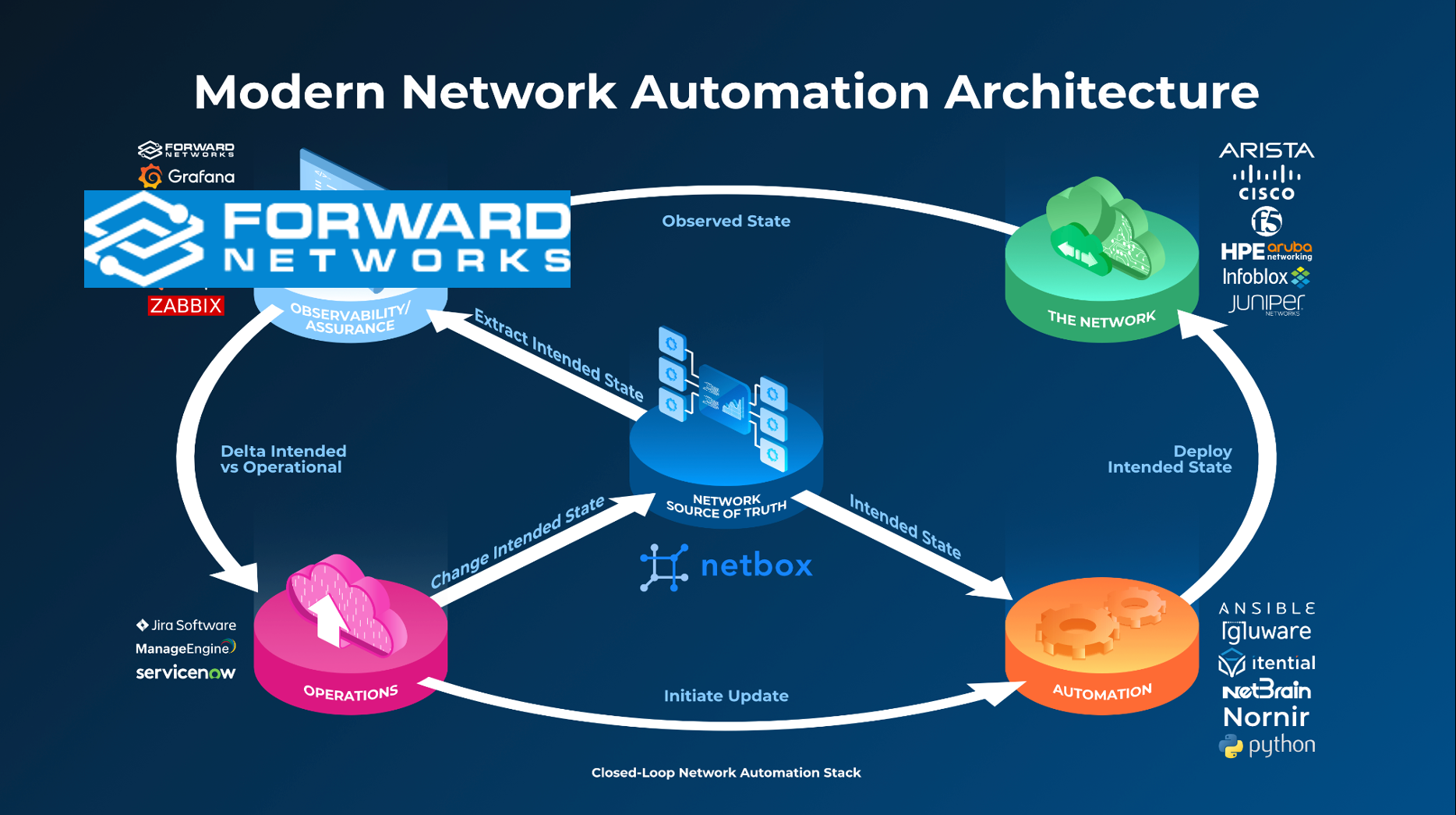
The first use case is about onboarding an empty NetBox instance with device data collected by Forward, such as Devices, Interfaces, Vendors, Location, and so forth.

The integration is based on a Python script.
It imports the data from Forward using NQE queries via REST APIs, transform the data from the Forward to the NetBox schema and then exports it to NetBox
The process can be automated using a web-hook so that NetBox is updated every time Forward collects from the network.
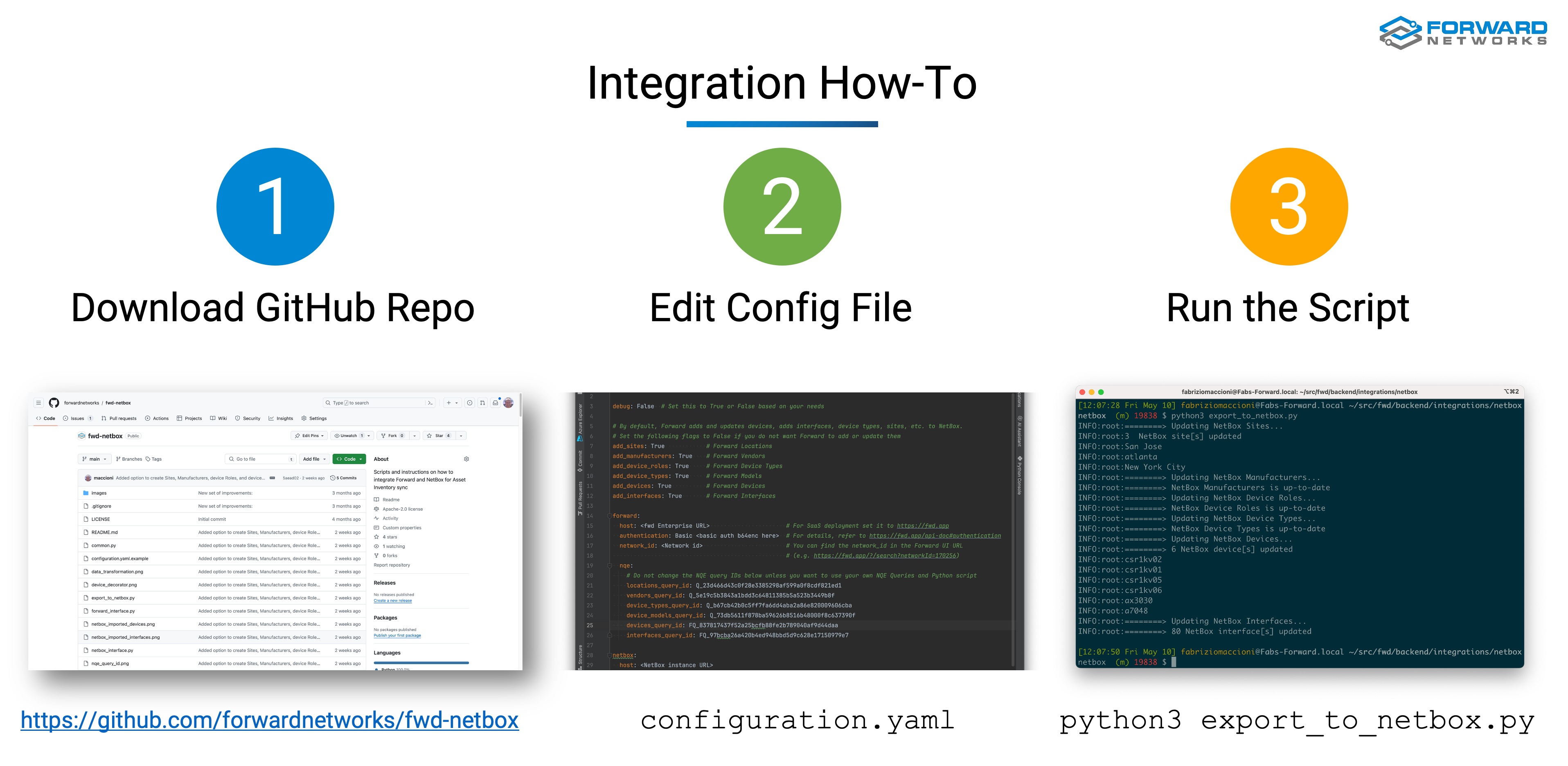
To run the integration, there are 3 easy-to-follow steps. First, download the public GitHub repo, then, edit a configuration file (more on this later), and, finally, run the script:
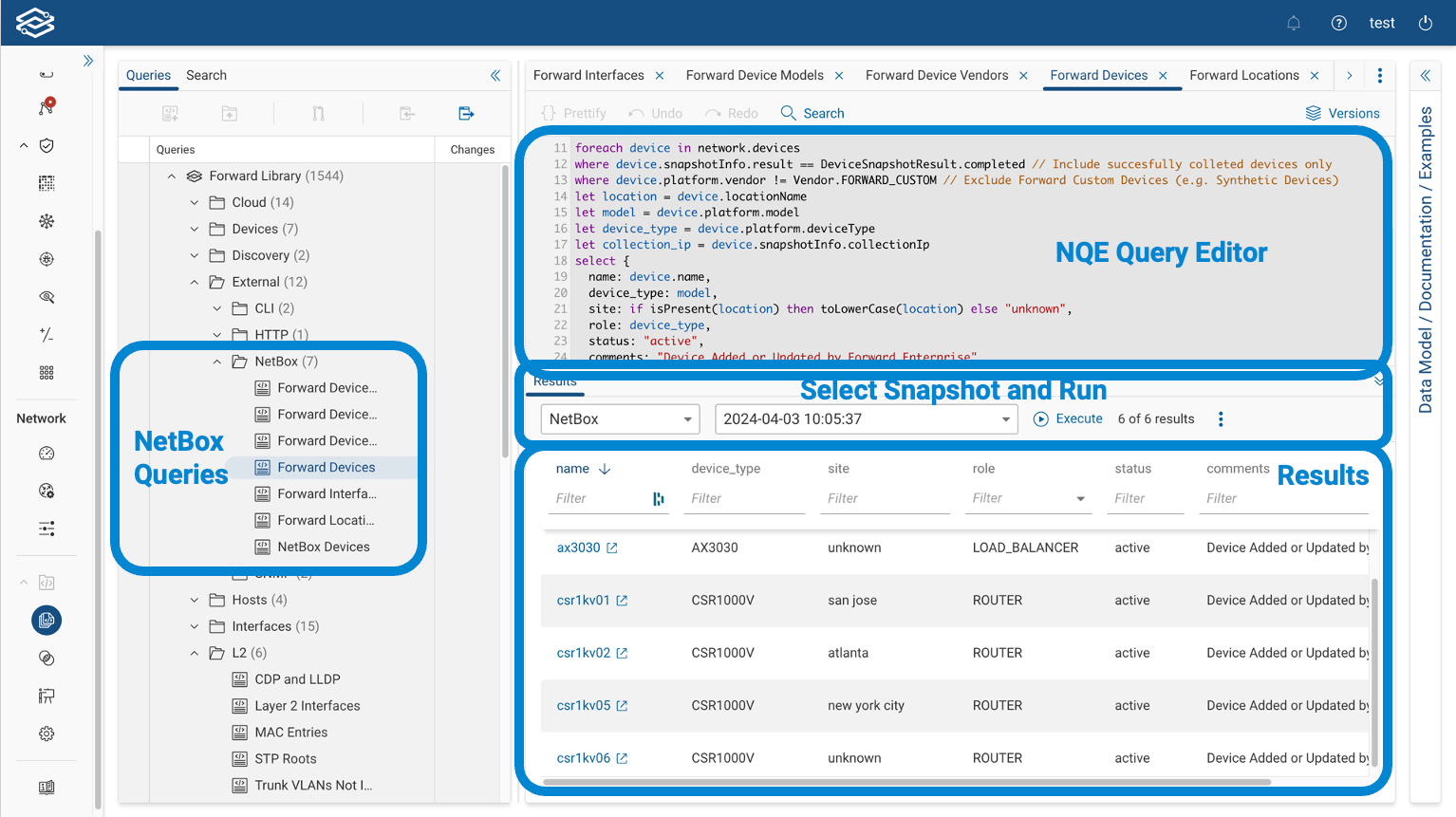
At the core of the integration is the Forward Network Query Engine, or NQE.
NQE is used to extract the Devices, Interfaces, Locations, etc. from Forward.
For this integration, you don’t need to write any query. All the queries are already included in the Forward Library, which is a collection of queries readily available to al Forward's customers.
The queries are referenced by IDs in the Python script.
The data needs to be transformed from the Forward to the NetBox schema before exporting it to NetBox.
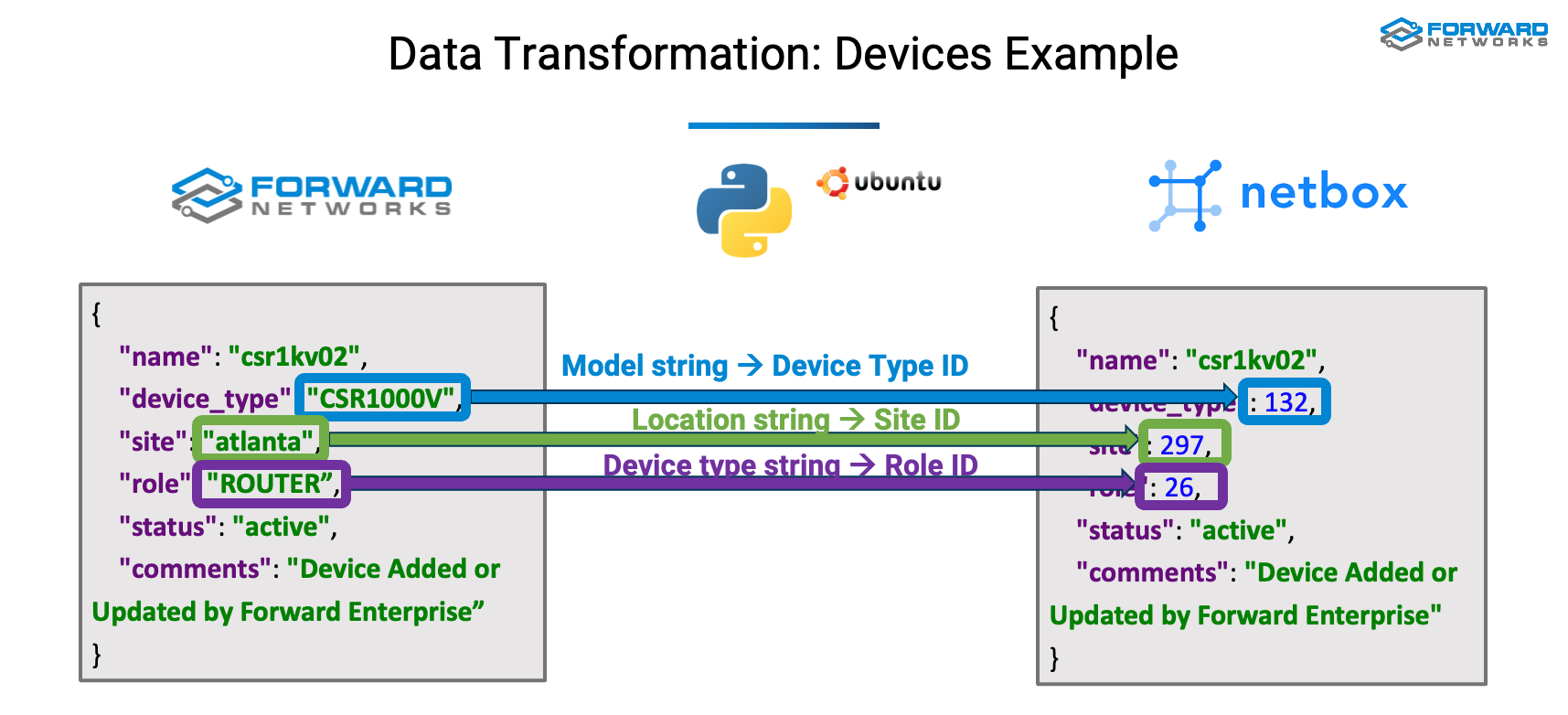
On the right side of the picture above, is shown an example of a REST API request for creating a Network device in NetBox. It’s a record of key:value pairs in JSON format.
On the left is shown the Forward NQE query response for the same device.
Notice that the keys are the same but some of the value types are different. For instance, the device_type is a string in Forward while it’s an ID in NetBox.
The Python scripts takes care of this translation by getting all the device types from NetBox and perform a lookup to find the corresponding ID.
Same for the Site and Role.
The same concept applies for creating Manufacturers, Interfaces, , Sites, etc
In short, the process includes query from Forward, data transformation and then export to NetBox.
There are only two sections required in configuration file.
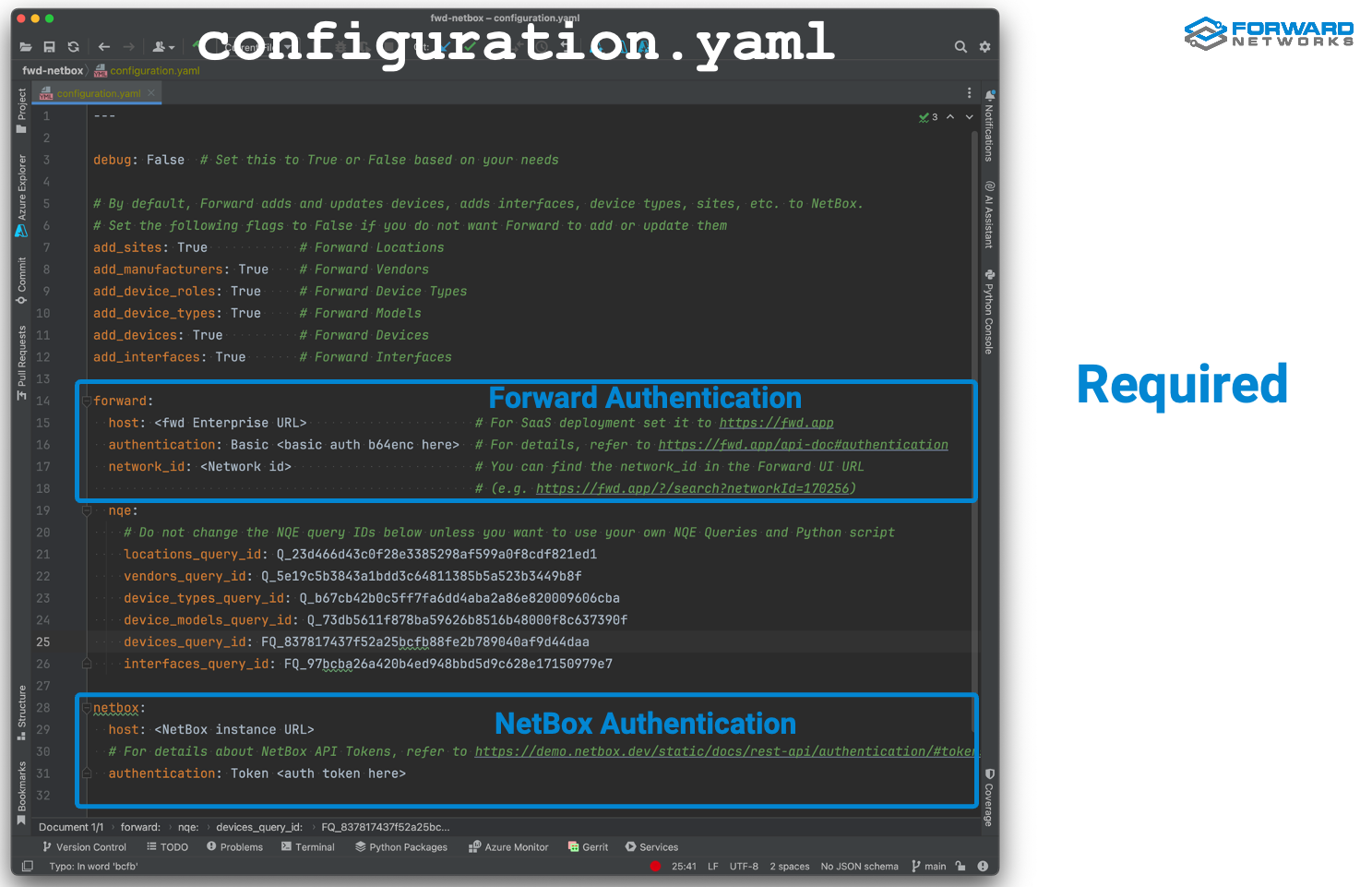
In the Forward section you need to provide URLs, authentication in base64 format and the Network ID.
Similarly, In the NetBox section you provide the instance URL and the authentication token
Optionally, you can turn on debug in case you run into any issue.
The section below is about what to export to NetBox. By default, the script will export everything. Sites, Roles, Devices, etc. but you can decide to not create some data by setting the flags to False. In this case you would need to make sure that the given Site, Role, etc. are already present in NetBox to make the integration work.
In the NQE section you can find all the IDs of the query published in the Forward NQE Library. There is no need to edit this section, unless you want to customize the integration with your own query and your python script customization.
On the screenshots below you can see a sample of what has been imported into NetBox:
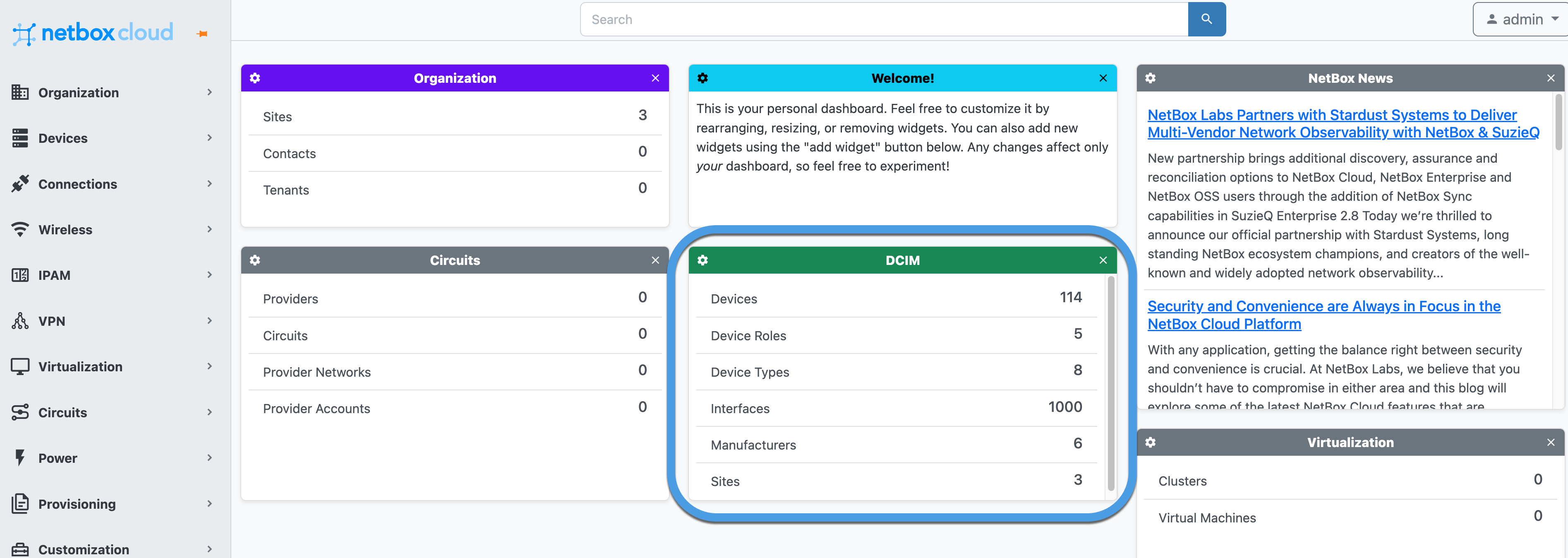
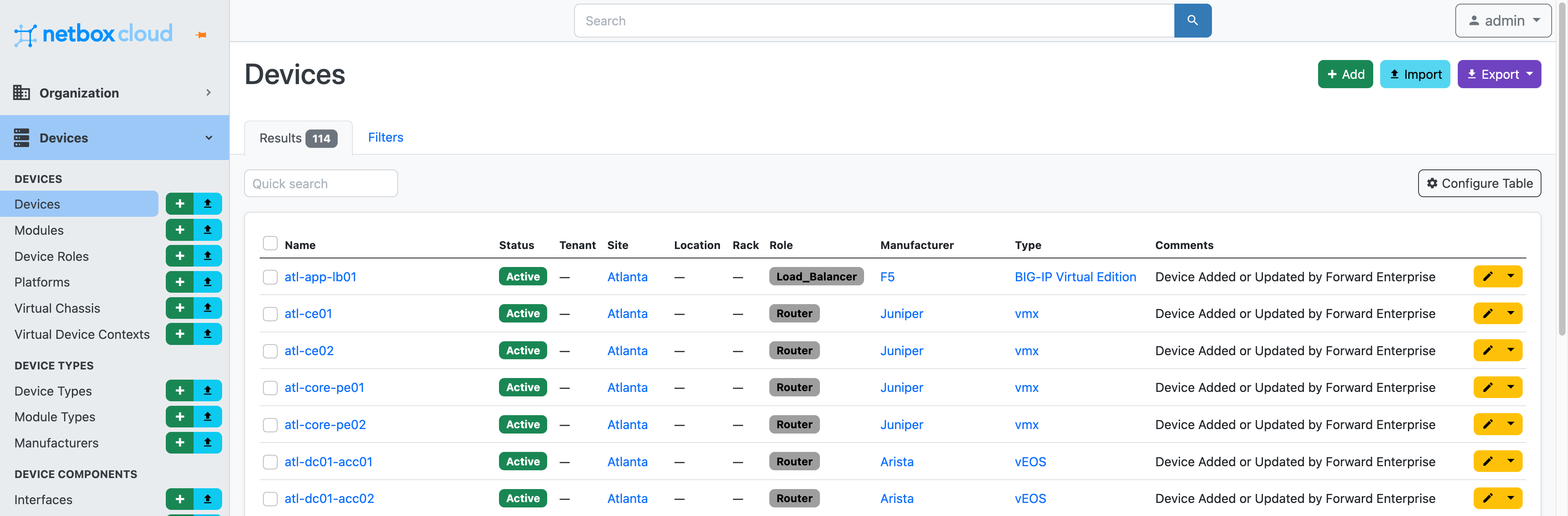
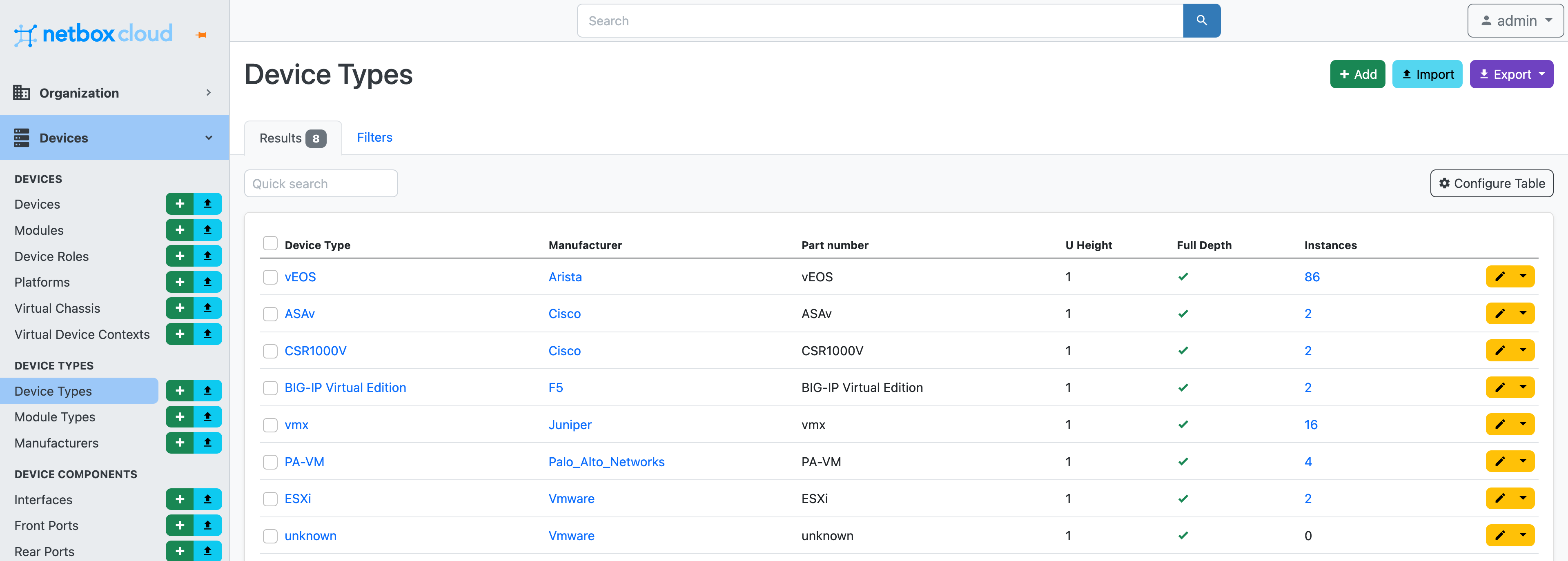
The second use case is about augmenting Forward with NetBox data. Specifically, how to use data that is not collected from Forward that is present in NetBox instead.
Data such as device racks and position, Tenants, Contacts, etc. that can be overlayed in existing Forward applications or used for instance for network compliance and auditing use cases.
This second use case is enabled by importing Device data from Netbox, and, by storing it in the Forward NQE.
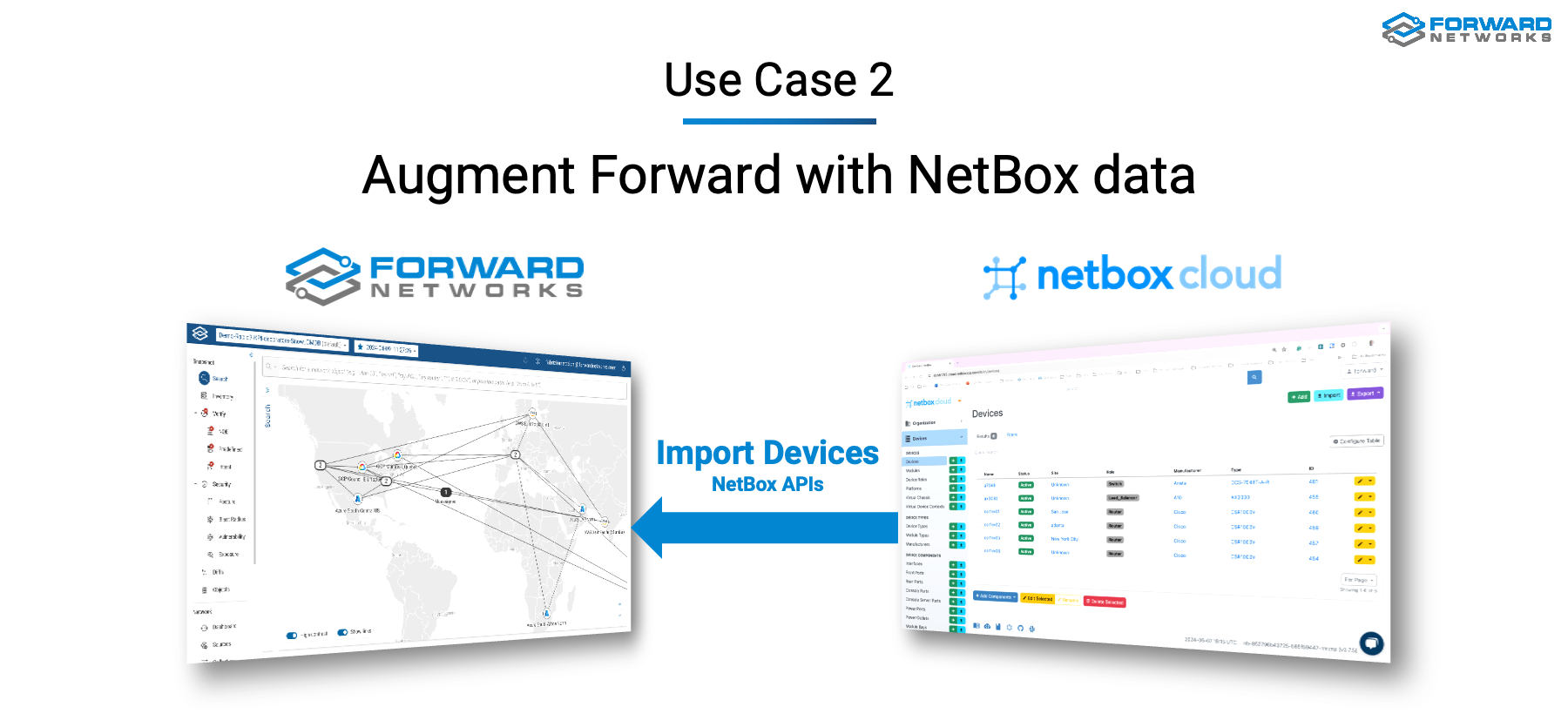
The imported data is parsed and its schema inferred to make it easier to be reused in NQE.
Once in NQE, the data it can be used in NQE queries, decorators and verifications.
The first example is about overlaying NetBox data in Forward applications such as like device cards in Search, or in a Path Analysis.
To do that, you can use the NetBox Devices query published in the Forward Library and use it to create a Forward device NQE decorator.
Navigating to the Search application and searching for a network device, it’ll show the device card in the middle pane.
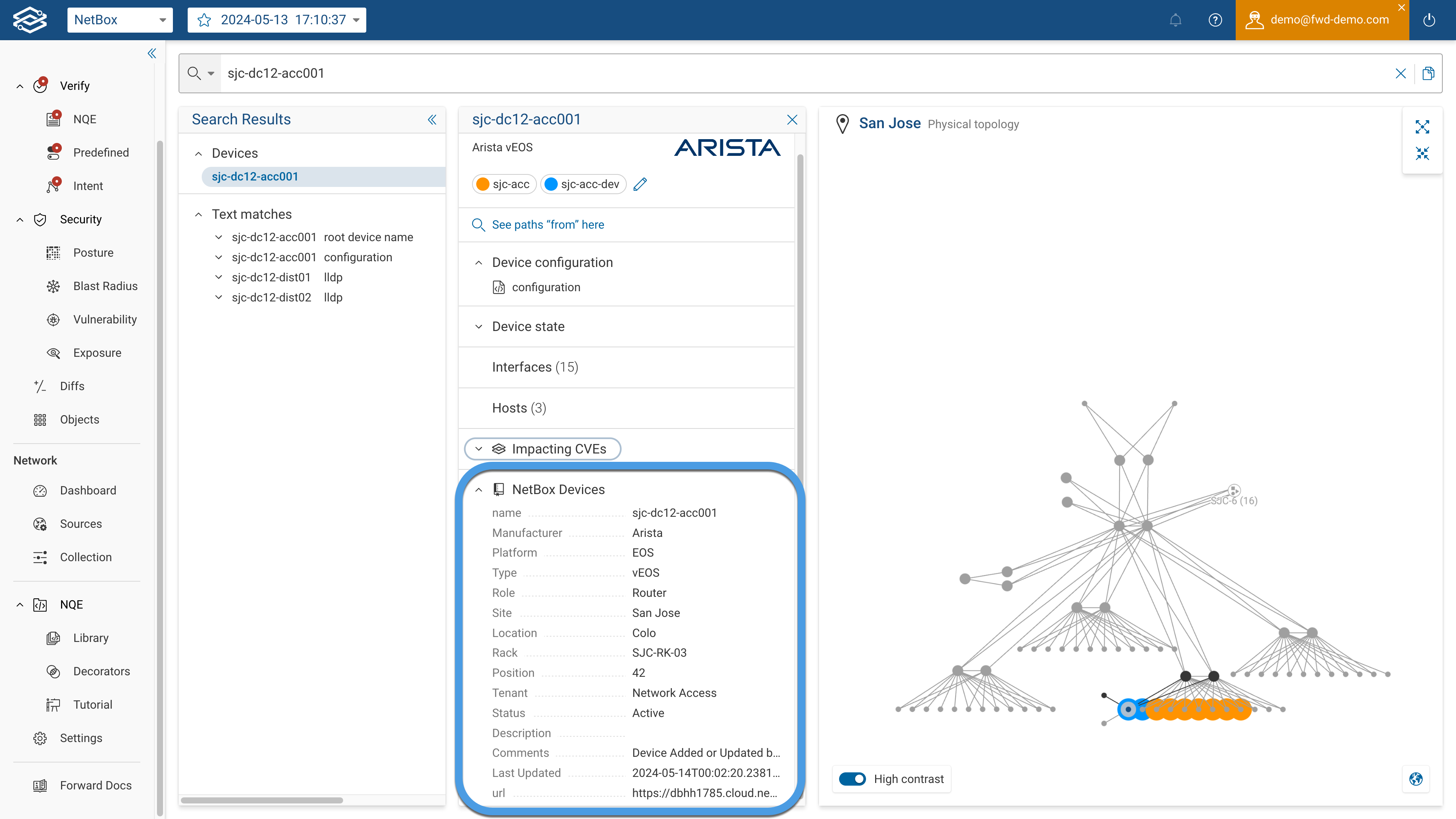
In the highlighted box you can see the output of the NetBox Devices query for the given device.
In the second example NetBox data is used in an auditing and compliance use case.
To do that, I’m going to use another existing NQE query. The CVE violations by device query that can be used to “Verify that every device is impacted by zero CVEs” across the entire network.
But what if my audit is about only a subset of the devices? For instance, only the devices managed by a given Business Unit or Tenant, say the Network Access team?
I can duplicate this query and use the Tenant information from NetBox to do exactly that!
The screenshot below shows you the added NQE statements
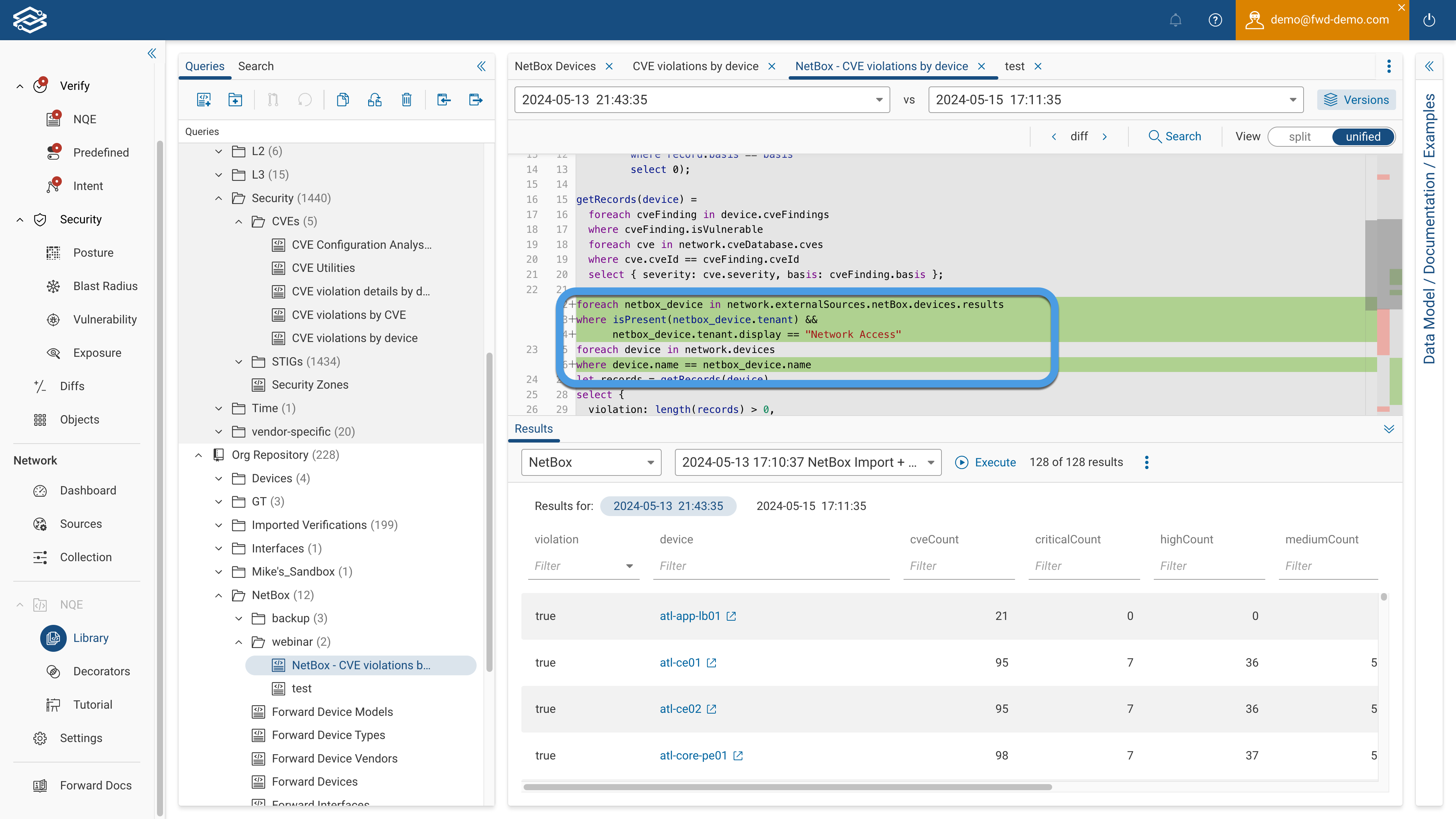
The query now loops trough all the devices in NetBox, select only devices with the Tenant set to Network Access with the same name as the device in Forward.
Executing the query you can verify if any of the devices managed by the Access Team have vulnerabilities in them. There are 12 of them in this network!!
I can now use the same query as an NQE verification to verify if there are vulnerabilities in those devices every time that Forward collects from the network and from NetBox.
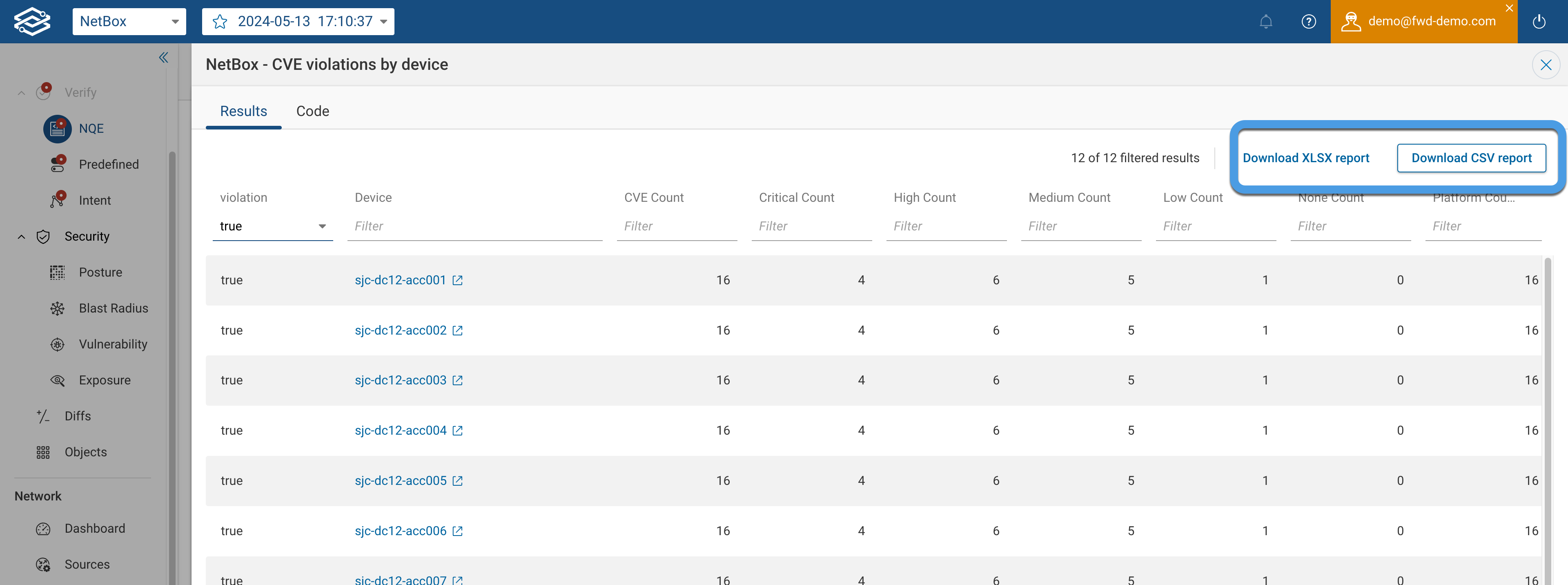
In the screenshot above, you can see the output of the NQE verification, which is currently failing because all 12 devices with vulnerabilities. Forward can then send notification via Slack, open an incident in Service Now, or download and share the report with the security teams or auditors.
To learn more about the integration, check the public GitHub Repository which provides non only the code but also a detailed description of the integration and how to run it






