I was asked to do pull all the password encryption methods for Cisco (route-switch) devices from our security team.
Here are a couple of NQE that I wrote to send off to the security team, hopefully it might be of use to someone else. They are pretty simple but if anyone has recommendations to enhance or combine into a single script, lemme know!
Results:
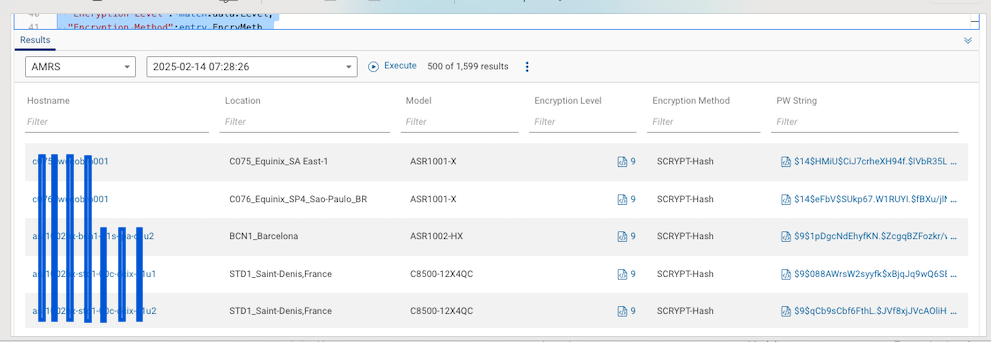
Nexus -
** Add custom command to collection for NX-OS Devices
show run | grep admin password
/**
* @intent Show encryption level and method on Cisco NX-OS devices
* Test
* @description Use CSV table below to match Encryption Level to Method
* add custom command for NXOS devices: show run | grep admin password
**/
Encrpytion =
"""csv
EncryLvl,EncryMeth
9,SCRYPT-Hash
5,MD5
4,SHA256
10,SHA512
7,Cisco_Type7-Algorithm
0,No-Encryption
""";
pattern1 = ```
{username:string} {admin:string} {PW:string} {Level:number} {str:string} {role:string} {NA:string}
```;
foreach device in network.devices
let platform = device.platform
where platform.os == OS.NXOS
// If you want to filter more with tags or some combination of Tags
//where "Cisco" in device.tagNames && "Network" in device.tagNames
foreach command in device.outputs.commands
where command.commandText == "show run | grep \"admin password\""
let filtered_response = replace(command.response, "-", "")
let blocks = parseConfigBlocks(OS.NXOS, command.response)
foreach match in blockMatches(blocks, pattern1)
//
// use csv table above to pull out encryption method
foreach entry in Encrpytion
where entry.EncryLvl == match.data.Level
let method = entry.EncryMeth
//
select {
Hostname:device.name,
"Location":device.locationName,
"Model": device.platform.model,
"Encryption Level": match.data.Level,
"Encryption Method":entry.EncryMeth,
"Password":match.data.str,
}IOS-XE -
** Add custom command to collection for all IOS Devices
show run | inc enable secret
/**
* @intent Show encryption level and method on Cisco IOS devices
* Test
* @description Use ecryption CSV table below to match Encryption Level to Method
**/
Encrpytion =
"""csv
EncryLvl,EncryMeth
9,SCRYPT-Hash
5,MD5
4,SHA256
10,SHA512
7,Cisco_Type7-Algorithm
0,No-Encryption
""";
pattern1 = ```
{Enable:string} {Secret:string} {Level:number} {PW:string}
```;
foreach device in network.devices
let platform = device.platform
where platform.os == OS.IOS_XE || platform.os == OS.IOS
// If you want to filter more - use tags or some combination of tags
// where "Cisco" in device.tagNames && "Network" in device.tagNames
foreach command in device.outputs.commands
where command.commandText == "show run | inc enable secret"
let filtered_response = replace(command.response, "-", "")
let blocks = parseConfigBlocks(OS.IOS, filtered_response)
foreach match in blockMatches(blocks, pattern1)
//
// use csv table above to pull out encryption method
foreach entry in Encrpytion
where entry.EncryLvl == match.data.Level
let method = entry.EncryMeth
//
select {
Hostname:device.name,
"Location":device.locationName,
"Model": device.platform.model,
"Encryption Level": match.data.Level,
"Encryption Method":entry.EncryMeth,
"PW String":match.data.PW,
}











