After spending the last 8 weeks as an intern, I’ve learned a lot about network digital twins and how they enhance visibility, maintenance, and security. You can read more about my experience in this post. Over the last few weeks, I’ve created powerful scripts to answer common security and compliance questions that years ago would have taken hours trying to answer in the CLI. The query I created below identifies Arista devices that have a security vulnerability in their configuration.
Benefit of this NQE
This query solves similar issues to those I encountered at previous network admin jobs. This query drastically cut the time I would have otherwise spent investigating issues on individual devices. With a little effort in creating this query, I can now answer these questions in seconds with each new network snapshot.
What this NQE does
The script identifies all Arista devices on the network that are missing the enable password xxxXXX command. This could be a policy driven configuration that all devices must adhere to, and you are responsible for identifying them. The enable password is intended to prevent unauthorized users from having access to privileged controls such as making configuration changes and adds another layer to the security posture of your network.
How this NQE works
- Create a pattern of text to be matched within the configuration of each device in the network
- Iterate over each device in the network where the vendor is Arista
- Enumerate the sum of devices in the network where the pattern matches the configuration
- Identify whether the configuration is present or not (violation) and list the device information: device name, location, and management IP address
- By leveraging the power of NQE, you can use your automation platform to remediate the violation, e.g., create a ServiceNow ticket
- Lastly, I provided a headline and description of the query to show the intent
Watch the video below for some NQE best practices such as using consistent terminology, not repeating yourself, defining column names that communicate well, and saving your code consistently, so you don’t break something.
/**
* @intent Identify any Arista devices without an enable password.
* @description Create a block of text that resembles a configuration.
* Query each device in the network where the vendor is Arista.
* Analyze the running configuration to check for enable password.
* Identify all violations and list device name, location, & mgmt IP.
*/
arista_enable_password_not_sha=```
enable password sha512
```;
foreach device in network.devices
where device.platform.vendor == Vendor.ARISTA
let conf = device.files.config
let count = length(foreach match in blockMatches(conf, arista_enable_password_not_sha) select match)
select {
violation : count==0,
deviceName: device.name,
location : device.locationName,
mgmtIP : device.platform.managementIps
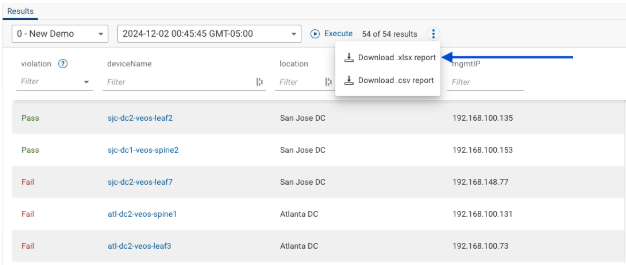
}Once the query is ready for execution, it’s good practice to first predict what the outcome should look like. This will help with understanding what may be missing, what went wrong, or how the query could be more helpful. Initially, my query only collected the devices that matched the pattern, but this left out crucial information, the devices that did not match the pattern. The code was revised to set a violation column and list all devices. The denominator in this scenario is important for trends and analysis. A report of the results can be generated as indicated by the blue arrow in the picture below.
In a separate post, I’ll go into detail on how this query can be modified to hit on a network of mixed vendors. What types of queries have helped you cut time from your regular workload?




