How can i add Custom command for fortinet.
command that i am looking.
- show system dns.
- show system ntp.
- show system central-management config system central-management.
How can i add Custom command for fortinet.
command that i am looking.
Check out the Docs in the following link. One needs to be logged into the FN Platform to see the Docs.
https://fwd.app/docs/enterprise/getting_started/configure_collection/devices/custom_commands/
There is a Fortinet example here:
That should get you started. There are quite a few examples of parsing Custom Commands in the Community. Let us know if you get stuck or have additional questions. Note that one needs to run a Snapshot to execute the Custom Commands.
Thanks
Hi Rohit,
when you follow the custom guide command documentation, your commands should look like this:
***
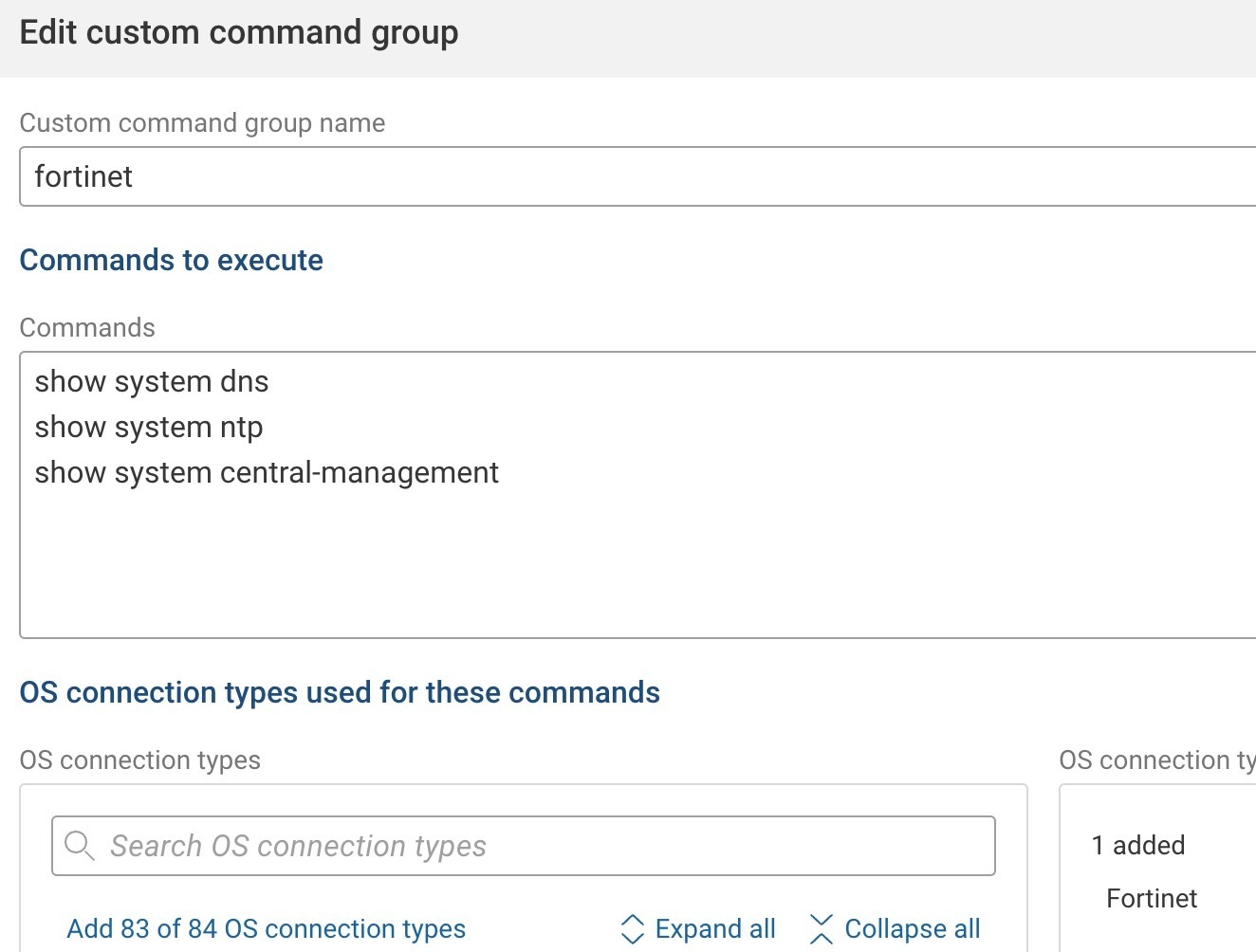
***
after you click save it should look like this:
***
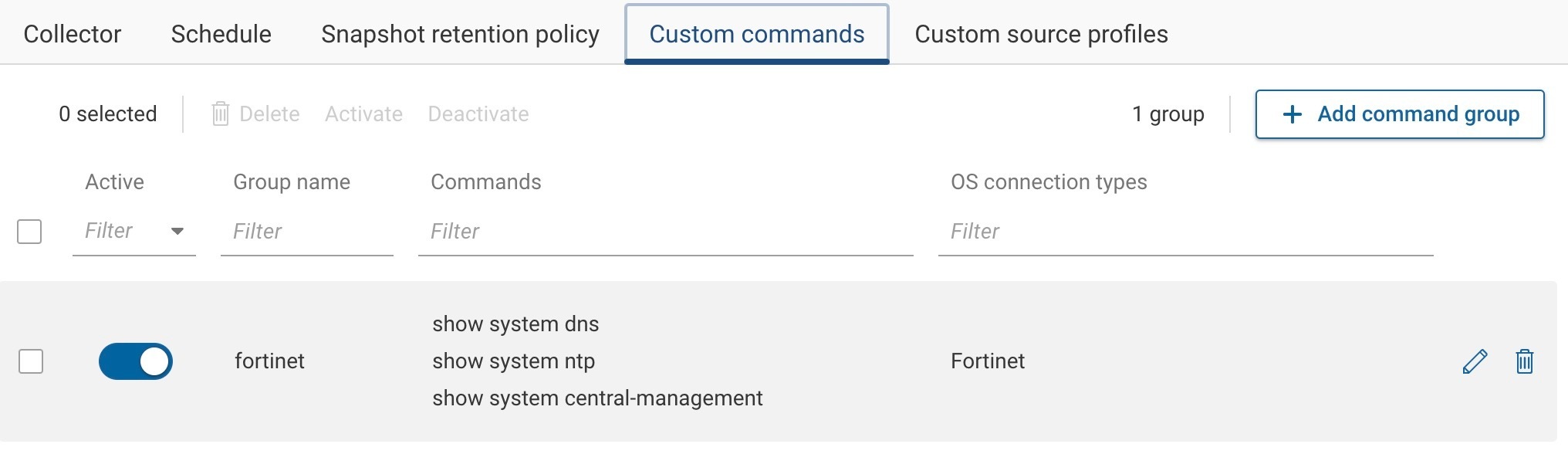
***
After that, you need to take a new Snapshot.
after the Snapshot has been processed, the output of the commands will be presented like this:
***
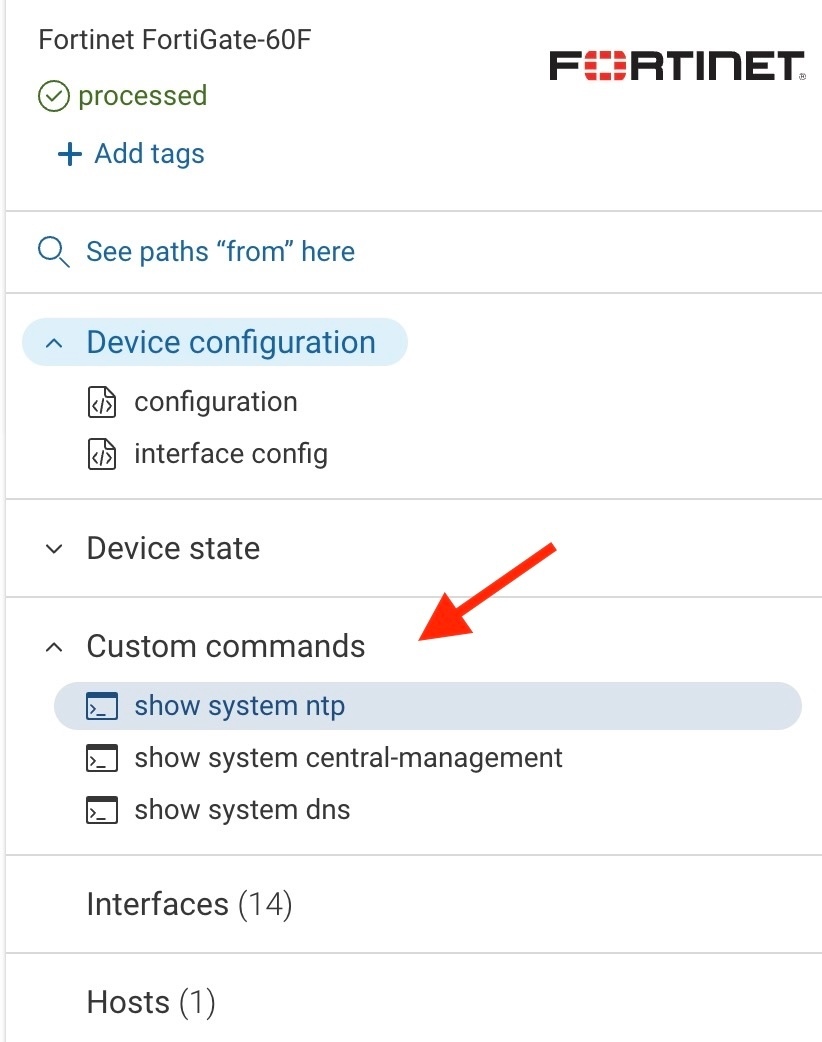
***
now, you can use an NQE query to search for information.
For example, you can use following NQE to parse the custom command responses for DNS Server information:
pattern_dns =
```
config system dns
set primary {pdns:string}
set secondary {sdns:string}
```;
foreach device in network.devices
where device.platform.vendor == Vendor.FORTINET
let outputs = device.outputs
foreach command in outputs.commands
where command.commandType == CommandType.CUSTOM
where command.commandText == "show system dns"
let configurations = parseConfigBlocks(OS.FORTINET, command.response)
foreach match in blockMatches(configurations, pattern_dns)
select {
deviceName: device.name,
"primary DNS": match.data.pdns,
"secondary DNS": match.data.sdns
}I hope it helps.
Excellent , getting the data now for NTP.
but i am trying to get the NTP details as well and i am using below NQE
pattern_dns =
```
config ntpserver
edit 1
set server1 {PNTP:string}
next
edit 2
set server2 {SNTP:string}
```;
foreach device in network.devices
where device.platform.vendor == Vendor.FORTINET
let outputs = device.outputs
foreach command in outputs.commands
where command.commandType == CommandType.CUSTOM
/* where command.commandText == "show system ntp" */
let configurations = parseConfigBlocks(OS.FORTINET, command.response)
foreach match in blockMatches(configurations, pattern_dns)
select {
deviceName: device.name,
"primary DNS": match.data.PNTP,
"secondary DNS": match.data.SNTP
}
and however i am getting zero result.
Hi
Can you try following pattern:
config system ntp
config ntpserver
edit 1
set server {PNTP:string}
edit 2
set server {SNTP:string}
Awesome , getting the output that we need , thanks
this is the format that currently i am using.
end
config global
show system dns
show system ntp
i hope it will not impact anything
these custom commands are sufficient to collect DNS and NTP information:
show system dns
show system ntphere is my config
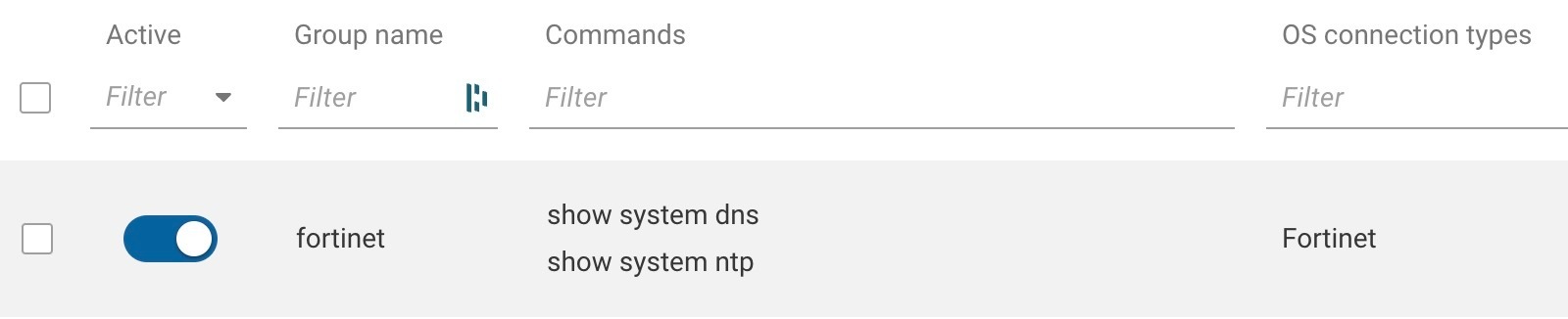
i am trying to get the fortimanger collected data from NQE , however due to some issue , i am not able to see all 3 ip’s in my NQE outpu t ,i am using below pattern.
config system central-management
set type fortimanager
set serial-number cccccccccccccccccc
set fmg "x.x.x.x"
config server-list
edit 1
set server-address c.c.c.c
next
edit 2
set server-address c.c.c.c
next
end
end
want to disaply all 3 c output, if noting is their ,balnk should be fine
Hi Rohit,
the previous pattern match expected to have exactly two NTP servers configured.
This NQE provides all any NTP Servers configured on Fortinet devices:
pattern_ntp =
```
config system ntp
config ntpserver
edit {editNumber:number}
set server {serverIp:string}
```;
foreach device in network.devices
where device.platform.vendor == Vendor.FORTINET
let outputs = device.outputs
foreach command in outputs.commands
where command.commandType == CommandType.CUSTOM
where command.commandText == "show system ntp"
let configurations = parseConfigBlocks(OS.FORTINET, command.response)
foreach match in blockMatches(configurations, pattern_ntp)
select {
deviceName: device.name,
ntpserver: match.data.serverIp
}
config system central-management
set type fortimanager
set serial-number cccccccccccccccccc
set fmg "x.x.x.x"
config server-list
edit 1
set server-address c.c.c.c
next
edit 2
set server-address c.c.c.c
next
end
end
Hi Rohit,
Does this help?
Kind regards,
Andy
/**
* @intent Find fortimanagers and update servers configured in Fortigates
* @description
*/
// Patterns to match
pattern_fmg = ```
config system central-management
set fmg {fmgIp:string}
```;
pattern_servers =
```
config system central-management
config server-list
edit {editNumber:number}
set server-address {serverAddr:string}
```;
// Loop through list of devices finding those that are Fortinet
// and store outputs of commands in the 'outputs' variable
foreach device in network.devices
where device.platform.vendor == Vendor.FORTINET
let outputs = device.outputs
// Loop through the commands in the outputs var, looking for custom
// commands that are from 'show system central-management' and store
// in a variable called central_mgmt
foreach command in outputs.commands
where command.commandType == CommandType.CUSTOM
where command.commandText == "show system central-management"
let central_mgmt = parseConfigBlocks(OS.FORTINET, command.response)
// Search for the two patterns looking for a match
foreach match in blockMatches(central_mgmt, pattern_fmg)
foreach server in blockMatches(central_mgmt, pattern_servers)
let servers = server.data.serverAddr
// Produce the results
select {
"Device Name": device.name,
"Fortimanager IP": match.data.fmgIp,
"Server IP": servers
}
I am getting the data from above NQE , but still i some devices data is missing. not able to see ip from this pattern “
pattern_fmg = ``` config system central-management set fmg {fmgIp:string} ```;
can you once more time.
can anyone please check and update me on this query ?
Can you verify the pattern you posted.
Could you please post the pattern as code? You can do it with clicking the three dots at the top right of the comment box and then select “Code”
Next please select language: “NQE” like this.
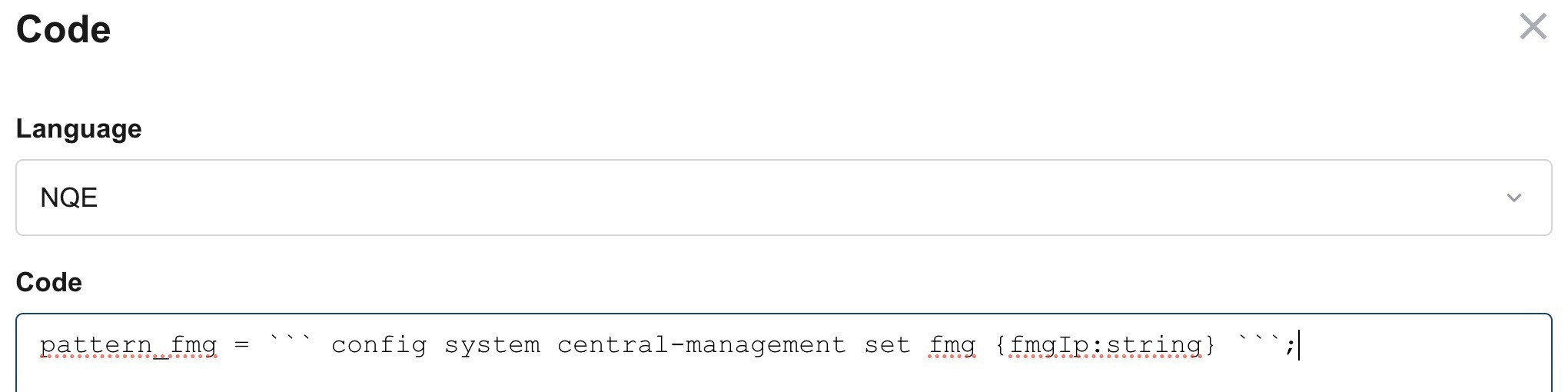
With block matching it is important to have the right indentation. There is a difference between this pattern match:
pattern_fmg = ``` config system central-management set fmg {fmgIp:string} ```;Here it is expected to have the string in one line
and this pattern match:
pattern_fmg =
```
config system central-management
set fmg {fmgIp:string}
```;Here the pattern match looks for the first line and then looks for a pattern in the second line, which is a subcommand to the first line.
I have tested the NQE from
Can you try if this NQE is what you need.
/**
* @intent Find fortimanagers and update servers configured in Fortigates
* @description
*/
// Patterns to match
pattern_fmg = ```
config system central-management
set fmg {fmgIp:string}
```;
pattern_servers =
```
config system central-management
config server-list
edit {string}
set server-address {serverAddr:string}
```;
// Loop through list of devices finding those that are Fortinet
// and store outputs of commands in the 'outputs' variable
foreach device in network.devices
/* where device.platform.vendor == Vendor.FORTINET */
let outputs = device.outputs
// Loop through the commands in the outputs var, looking for custom
// commands that are from 'show system central-management' and store
// in a variable called central_mgmt
foreach command in outputs.commands
where command.commandType == CommandType.CUSTOM
where command.commandText == "show system central-management"
let central_mgmt = parseConfigBlocks(OS.FORTINET, command.response)
// Search for the ""pattern_fmg" pattern looking for a match
foreach match in blockMatches(central_mgmt, pattern_fmg)
//loop through the all server-address IP's and store them in variable "servers"
let servers = (foreach server in blockMatches(central_mgmt, pattern_servers)
where server.data.serverAddr == server.data.serverAddr
select server.data.serverAddr)
// Produce the results
select {
"Device Name": device.name,
"Fortimanager IP": match.data.fmgIp,
"Server IP": servers
}
Awesome , this is working , i am getting the output that i need , Really Appreciate.
Thanks
Already have an account? Login
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.